React2Shell Exploitation Campaign Targeting Web3 Users

Executive Summary
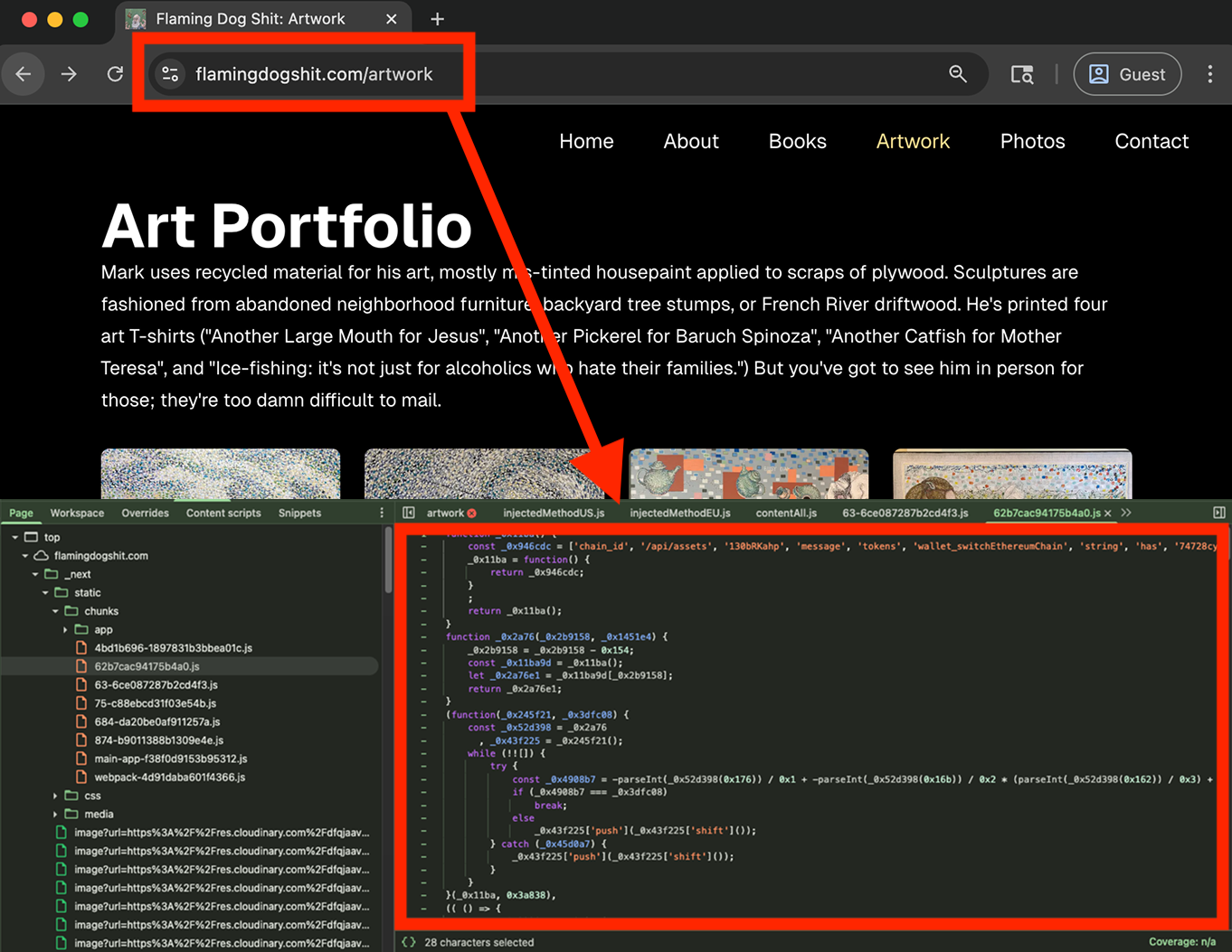
Blockaid has identified an ongoing, coordinated campaign in which a single threat actor compromised dozens vulnerable websites using React2Shell (CVE-2025-55182), a critical React Server Components vulnerability. The campaign highlights how vulnerabilities in standard Web2 frameworks can be weaponized to target Web3 users.
Key findings:
- The actor injected malicious JavaScript that triggers wallet connection prompts and leads victims into wallet-drainer transactions.
- Blockaid attributed receiver addresses used to collect stolen funds.
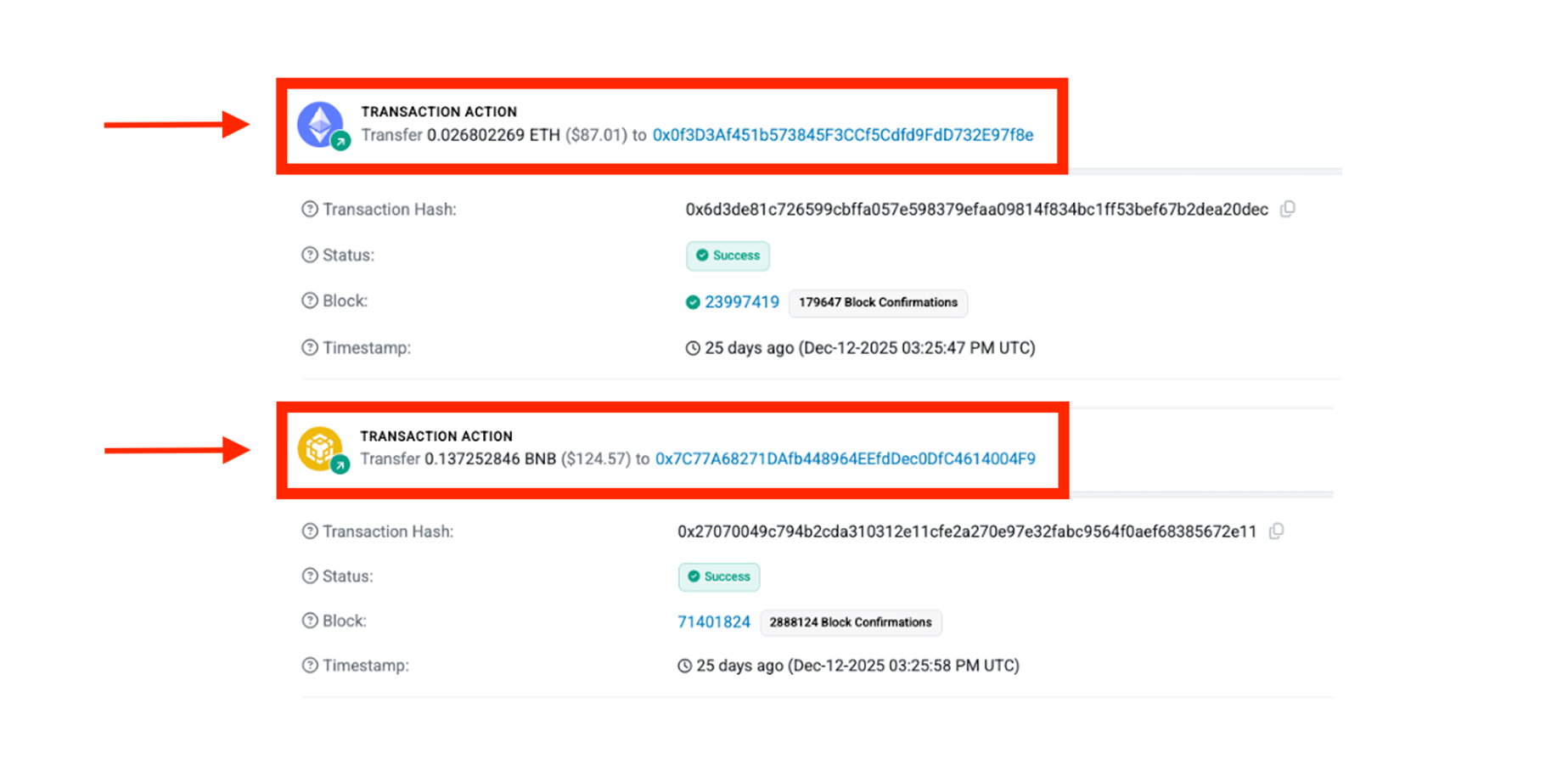
- Onchain analysis indicates theft of more than $10,378.44 USD in native assets since December 10, 2025, averaging ~$188 per transaction, impacting multiple EVM chains (Ethereum, BSC, Polygon, Arbitrum, Avalanche, Base).
- Blockaid has clustered the end-to-end infrastructure (compromised domains, drainer bytecode, proxy implementations, deployers); wallets integrated with Blockaid are protected.

Vulnerability
React2Shell (CVE-2025-55182) represents a critical vulnerability in React Server Components (RSC) that enables unauthenticated remote code execution with a maximum CVSS score of 10.0. Disclosed on December 3, 2025, the vulnerability affects React versions 19.0.0 through 19.2.0. It was initially tracked as CVE-2025-55182 (React) and CVE-2025-66478 (Next.js), but the latter has since been rejected as a duplicate.
Exploitation activity began shortly after public disclosure, with over 4,100 attempts observed within the first two hours.
Web3 Campaign
Blockaid has observed a coordinated effort where attackers successfully breached dozens of domains to inject malicious JavaScript targeting Web3 users. Based on the malicious payload, Blockaid clustered these attacks under one actor. The campaign is still ongoing and highlights how vulnerabilities in standard Web2 frameworks can be weaponized to target Web3 users.

TTPs and Infrastructure
- Initial vector: Hundreds of vulnerable websites were compromised by the actor to reach a broad audience of Web3 users. Attackers exploited the RSC flaw to inject malicious JavaScript directly into the front-end of these Web2 legitimate websites.
- Targeting: Only several websites appear overtly crypto/trading-related. The diversity of TLDs and verticals (health, games, “dashboards,” SMB sites, etc.) strongly suggests scanner-driven exploitation rather than a sector-specific hit list.
- Malicious script: When users visited these compromised but otherwise trusted sites, the injected script would automatically trigger wallet connection prompts, attempting to trick users into interacting with a malicious interface.
- Funds theft: Users interacting with compromised sites were exposed to wallet drainer transactions.
- Attackers’ infrastructure: Blockaid identified multiple addresses to which stolen funds were sent.
Mitigation & Response
Blockaid identified and clustered the malicious infrastructure end-to-end: including compromised domains, drainer bytecode, proxy implementations, and deployer addresses.
Wallets integrated with Blockaid’s End User Protection were protected from this campaign, including major platforms such as Coinbase, MetaMask, Ledger, Trezor, Zerion, Trust Wallet, Backpack, Tangem, and Gemini with real-time alerts preventing users from signing malicious transactions.
Organizations must immediately update React packages to patched versions: react-server-dom-webpack to version 19.0.1, 19.1.2, or 19.2.1; react-server-dom-parcel and react-server-dom-turbopack to version 19.0.1 or later. For Next.js, update to versions 15.0.5, 15.1.9, 15.2.6, 15.3.6, 15.4.8, 15.5.7 for 15.x branch, or 16.0.7 for 16.x branch. Users are advised to be wary of unexpected wallet connection prompts on websites that do not typically require them, even if the site is well-known and legitimate.
Blockaid is securing the biggest companies operating onchain
Get in touch to learn how Blockaid helps teams secure their infrastructure, operations, and users.




