Why Chains Are Moving Policy and Threat Enforcement to the RPC Layer

Public blockchains are designed to be open. Anyone can create tokens, deploy contracts, and send transactions—permissionlessly.
But for chains aiming to serve enterprises, creators, or end users at scale, that openness introduces risk:
- Anyone can mint NFTs that infringe on IP
- Anyone can create scam tokens that mimic known assets
- Anyone can submit exploit payloads targeting your ecosystem
- Anyone can interact with your chain—including sanctioned actors
This creates a gap between what chains allow and what their stakeholders can accept. Compliance, trust & safety, and security teams have few tools to enforce the policies they need—especially in real time.
Traditional defenses miss the chain-level gap
Web3 has made big strides in threat detection. Wallets now warn users before they sign. Blocklists flag malicious domains. Transaction simulators expose phishing attempts before they land.
These protections are essential.
But if you're running a chain—or building the infrastructure others depend on—that’s not where your responsibility ends.
Blocklists are reactive. Most monitoring solutions detect threats after the damage is done. And none of them give you control over what gets included in your blockchain.
If your RPC layer accepts the transaction, and your sequencer includes it in a block, then your chain has participated in that threat—whether it was a scam token, an infringing NFT, or a sanctioned address.
You can’t leave enforcement to chance. You need control.
The missing layer: real-time policy enforcement at the RPC
Every transaction—legitimate or malicious—passes through your chain’s RPC layer before it reaches a sequencer or validator.
This is a critical—and underused—control point.
The eth_sendRawTransaction method is where users broadcast transactions to the network. It’s also where chain operators can intercept, simulate, inspect, and make decisions before a transaction is confirmed.
By inserting a validation layer at the RPC, chains can:
✅ Detect threats and policy violations before execution
✅ Block unsafe transactions deterministically
✅ Enforce trust, safety, and compliance controls at scale
Think of it like a firewall for your chain.
You don’t need to modify consensus. You don’t need to restrict developers. You just add a gateway that applies the rules your chain and your stakeholders require.
What this makes possible
By shifting enforcement to the RPC layer, chains can:
Stop threats before they hit the chain
Block phishing contracts, honeypots, rug pulls, and drainers before users interact with them. No alerts, no retroactive takedowns, just real-time prevention.
Enforce custom policy controls
Control what types of assets are allowed on your chain. Block infringing NFTs, impersonation tokens, or user-generated content that violates your terms of service or IP standards.
Ensure compliance by design
Prevent interaction with OFAC-sanctioned addresses, restricted jurisdictions, or illicit financial flows—automatically, without slowing down developers.
Protect your infrastructure
Stop sequencers, relayers, or nodes from being used as attack vectors. Block transaction-based DDoS attempts, exploit payloads, and abuse of system contracts.
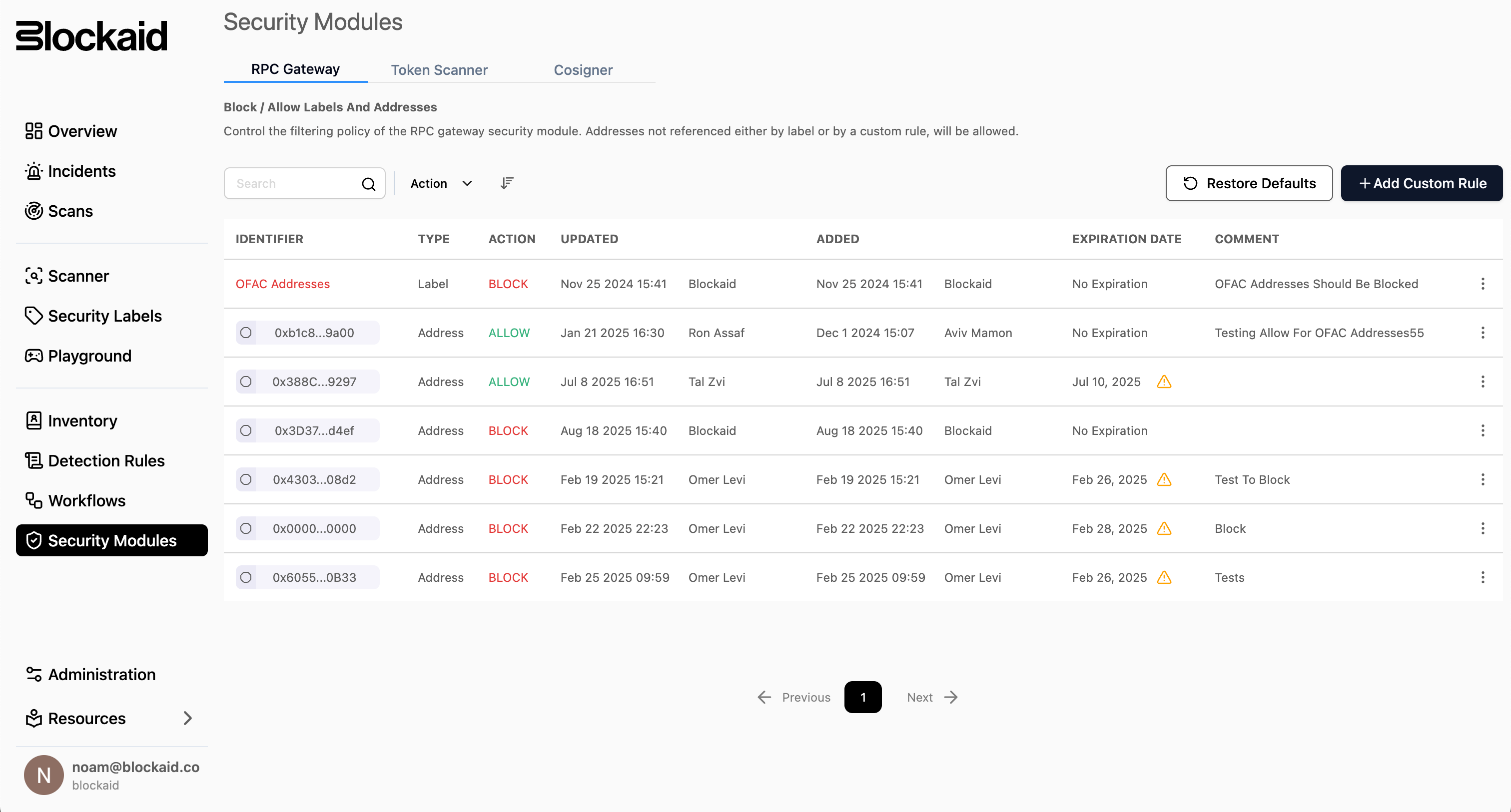
Blockaid’s RPC Gateway security module
For chains looking to implement this enforcement model, Blockaid provides an end-to-end RPC layer security stack.
It integrates directly into the transaction submission flow, inserting a validation proxy at the eth_sendRawTransaction call.
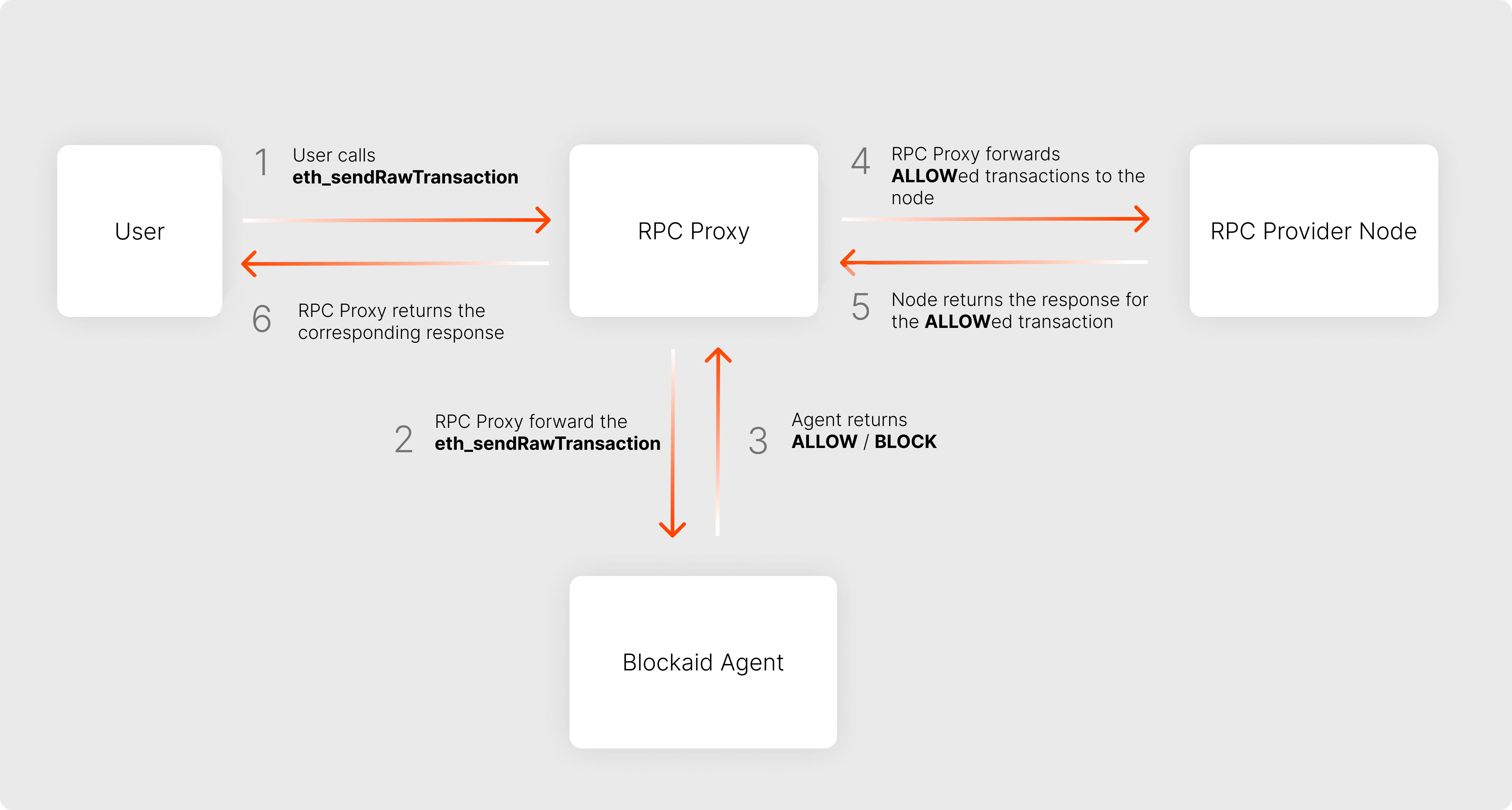
Every transaction is:
- Intercepted pre-submission
- Simulated and analyzed in real time using:
- Blockaid’s threat intelligence (e.g. scams, malware, exploits)
- Your custom policy rules (e.g. IP enforcement, sanctions enforcement)
- Verdict returned: ALLOW or BLOCK
- Only safe transactions are executed
For high-performance environments, the module supports local NGINX-based proxying to ensure minimal latency and enterprise-grade throughput.
Final Thoughts
You can’t secure a chain by reacting to threats after they’ve landed.
If you're building a chain designed for scale, brand integrity, or regulatory readiness, you need enforcement that happens before transactions reach the chain.
RPC-layer security provides the control you need without compromising openness, development velocity, or composability.
Blockaid helps leading chains move fast, stay compliant, and block what doesn’t belong. Want to see how it works in practice? Let’s talk.
Blockaid is securing the biggest companies operating onchain
Get in touch to learn how Blockaid helps teams secure their infrastructure, operations, and users.




