Transaction Verification: A Solution to Blind Signing in Hardware Wallets

Transaction simulations have greatly improved software wallet security by allowing users to review transaction details before signing. However, this improvement has not fully extended to hardware wallets.
Due to various limitations of hardware wallets, many of them fail to show meaningful transaction details at the point of signing.
Instead, users often rely on the information shown in the software counterpart of the hardware wallet, while relying on the assumption that the transaction they are about to sign on their hardware wallet is the same as the one they reviewed.
This whitepaper explores the problem of blind signing and a solution for ensuring secure, end-to-end transaction integrity.
Problem statement: Blind signing and the limitations of hardware wallets
Hardware wallets are designed to securely manage private keys offline and protect them from potential threats. However, they are not built to manage transaction security.
Instead, they rely on signing interfaces—applications on users’ devices that interact with dApps and handle transaction details.
Once a transaction is initiated, the signing interface sends the transaction data to the hardware wallet for signing. While the wallet confirms the request, it doesn't verify the transaction details.
This creates a gap in transaction integrity and security, as their role is limited to signing what’s passed from the interface without fully understanding or validating the specifics.
This weakness was highlighted in the Radiant Capital breach, where attackers compromised the device running the signing interface.
They displayed a legitimate transaction in the interface for users to review, but secretly sent a different, malicious transaction to the hardware wallet for signing.
As a result, the Radiant team unknowingly approved fraudulent transactions, leading to the loss of over $50 million.
This type of attack underscores the fundamental limitation of current hardware wallets: they do not independently verify a transaction's integrity or intent.
Relying on external interfaces leaves users vulnerable to man-in-the-middle attacks, where transaction data is manipulated after it’s displayed to the user but before it reaches the hardware wallet.
Although some progress has been made—such as Ledger’s Clear Signing initiative, which displays more detailed transaction information—the core issue remains.
Hardware wallets still lack the ability to fully validate the transaction being signed, leaving users at risk of blindly approving malicious transactions.
Solution: Transaction verification
Transaction verification is a proposed solution that addresses the vulnerability of blind signing by establishing a cryptographically verified connection between the transaction simulation and the transaction being signed.
It does so by introducing a new entity, called a verification provider, as an intermediary between the signing interface and the hardware wallet, ensuring that the transaction remains secure and unaltered from the time it’s reviewed by the user to when it is signed.
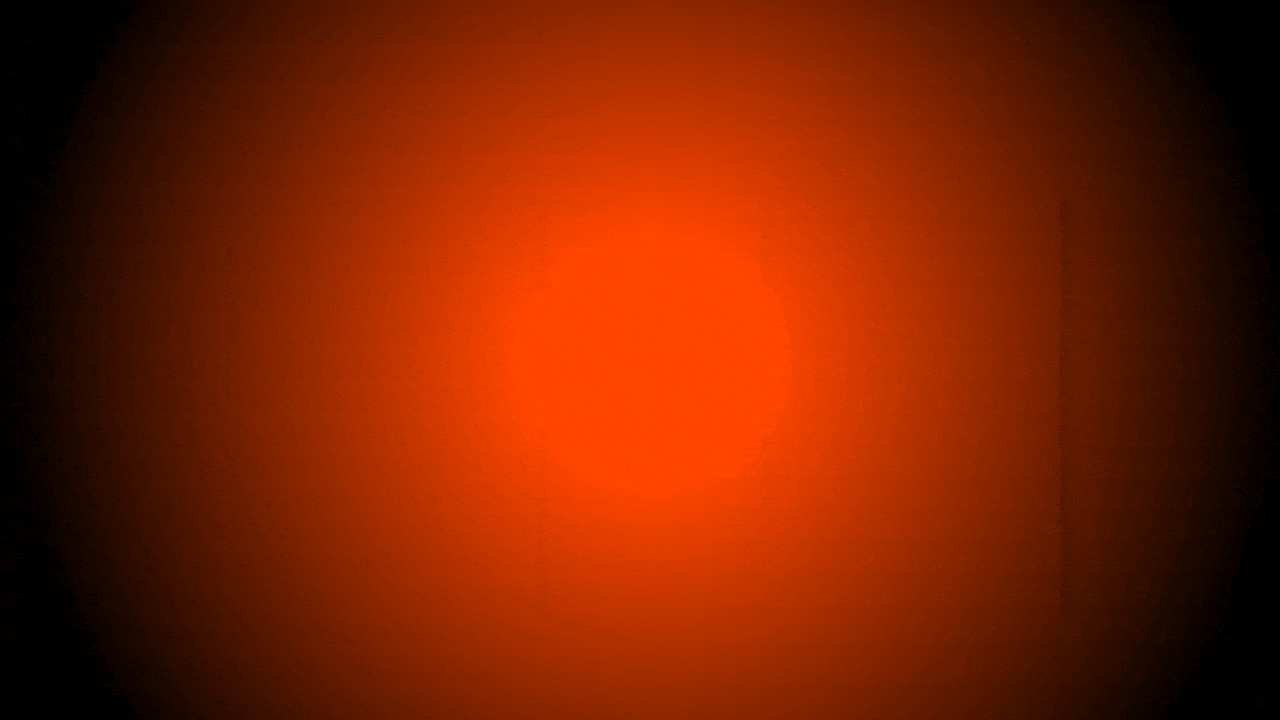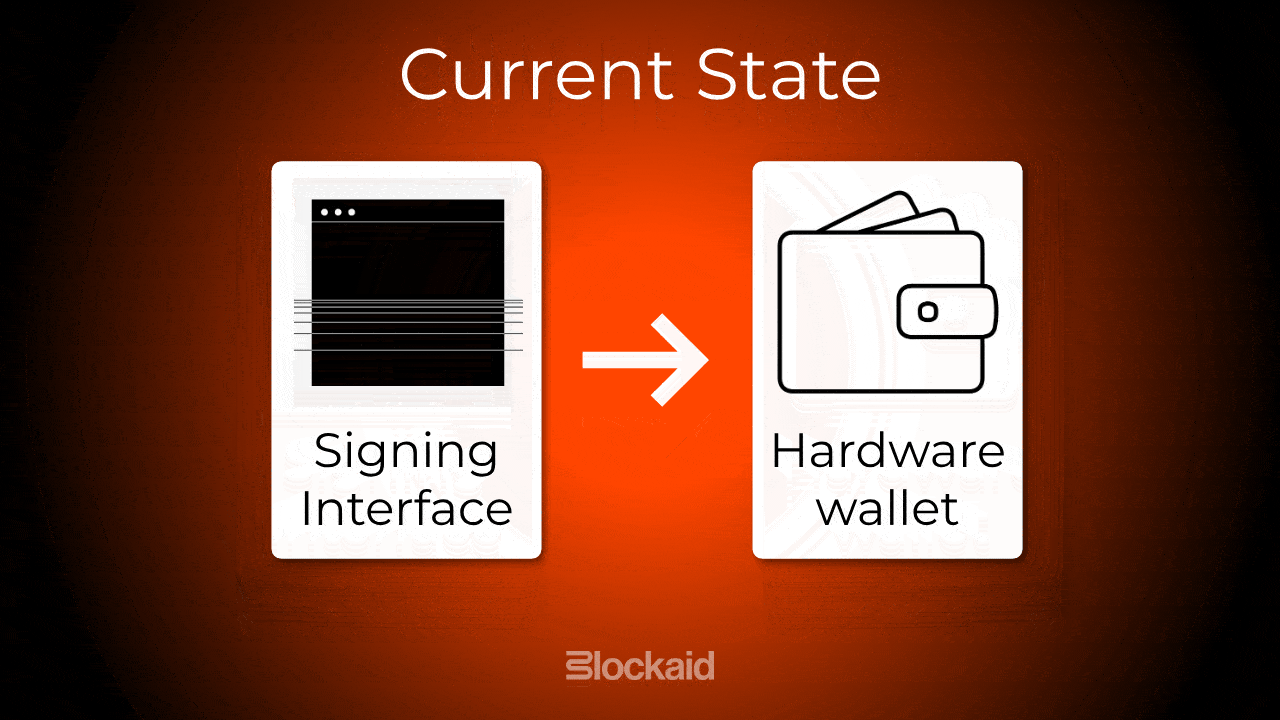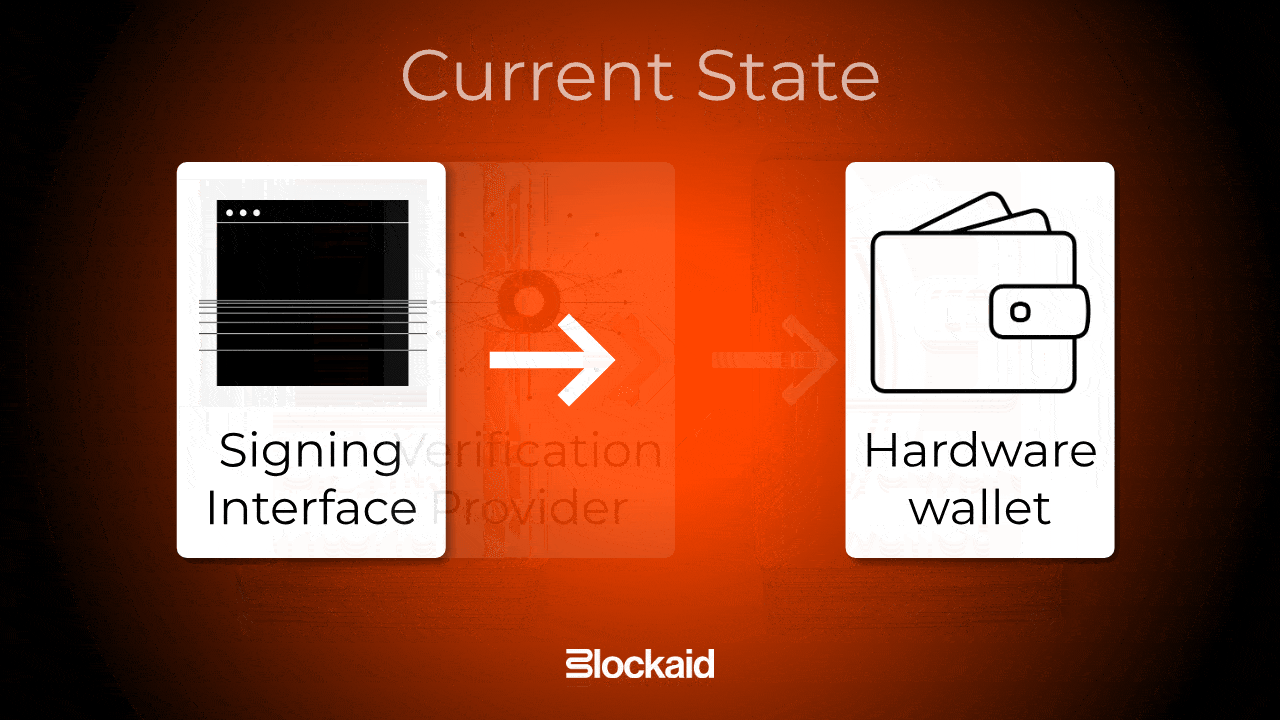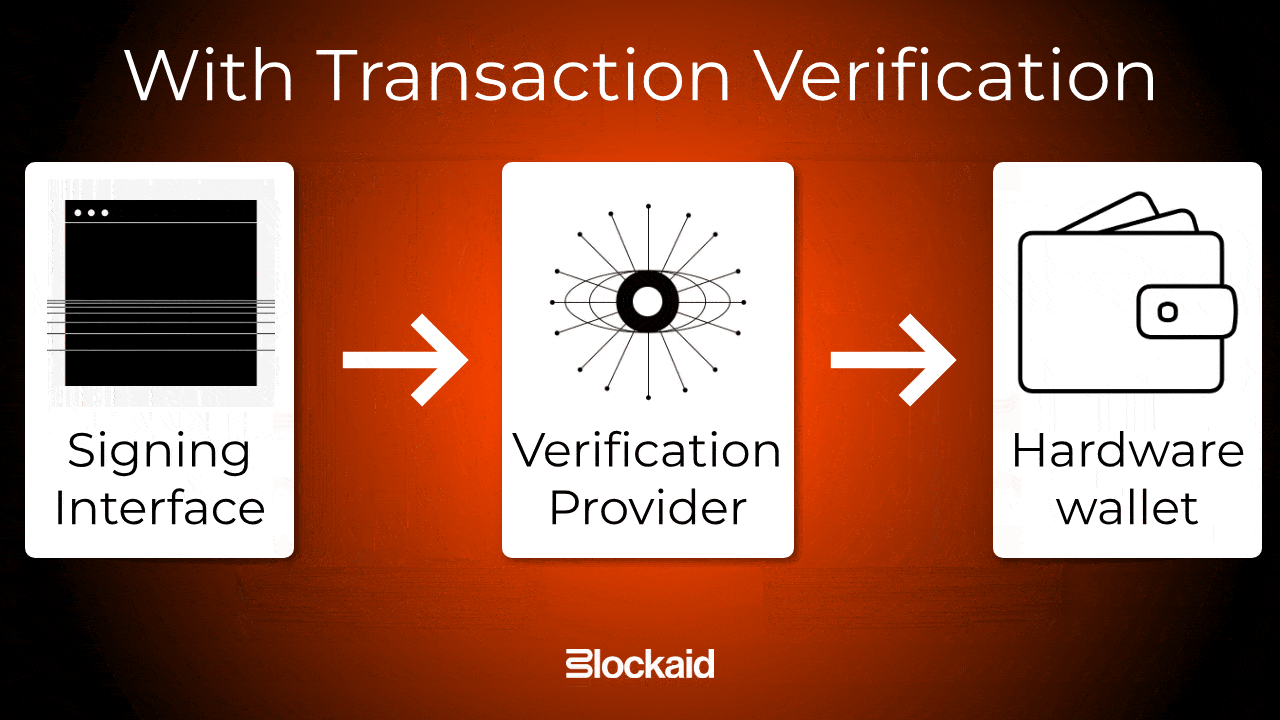
How transaction verification works
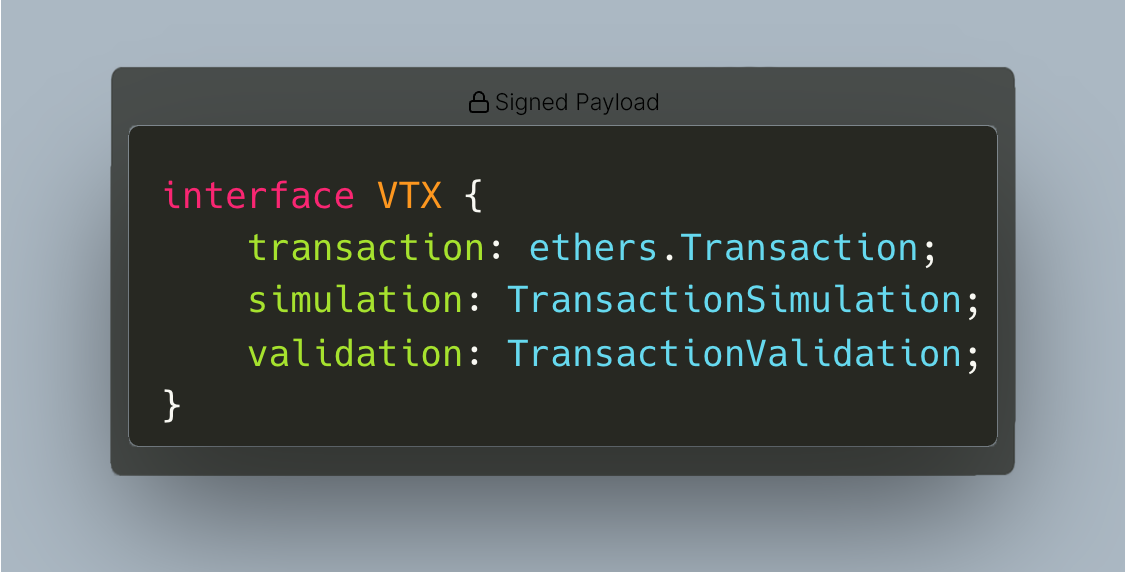
At the core of transaction verification is the verifiable transaction payload (VTX), which is generated by the verification provider.
The VTX bundles the transaction, its simulation, and validation results into a single cryptographically signed payload that guarantees the integrity of the transaction and provides verifiable security to the hardware wallet.
Here’s how it works:
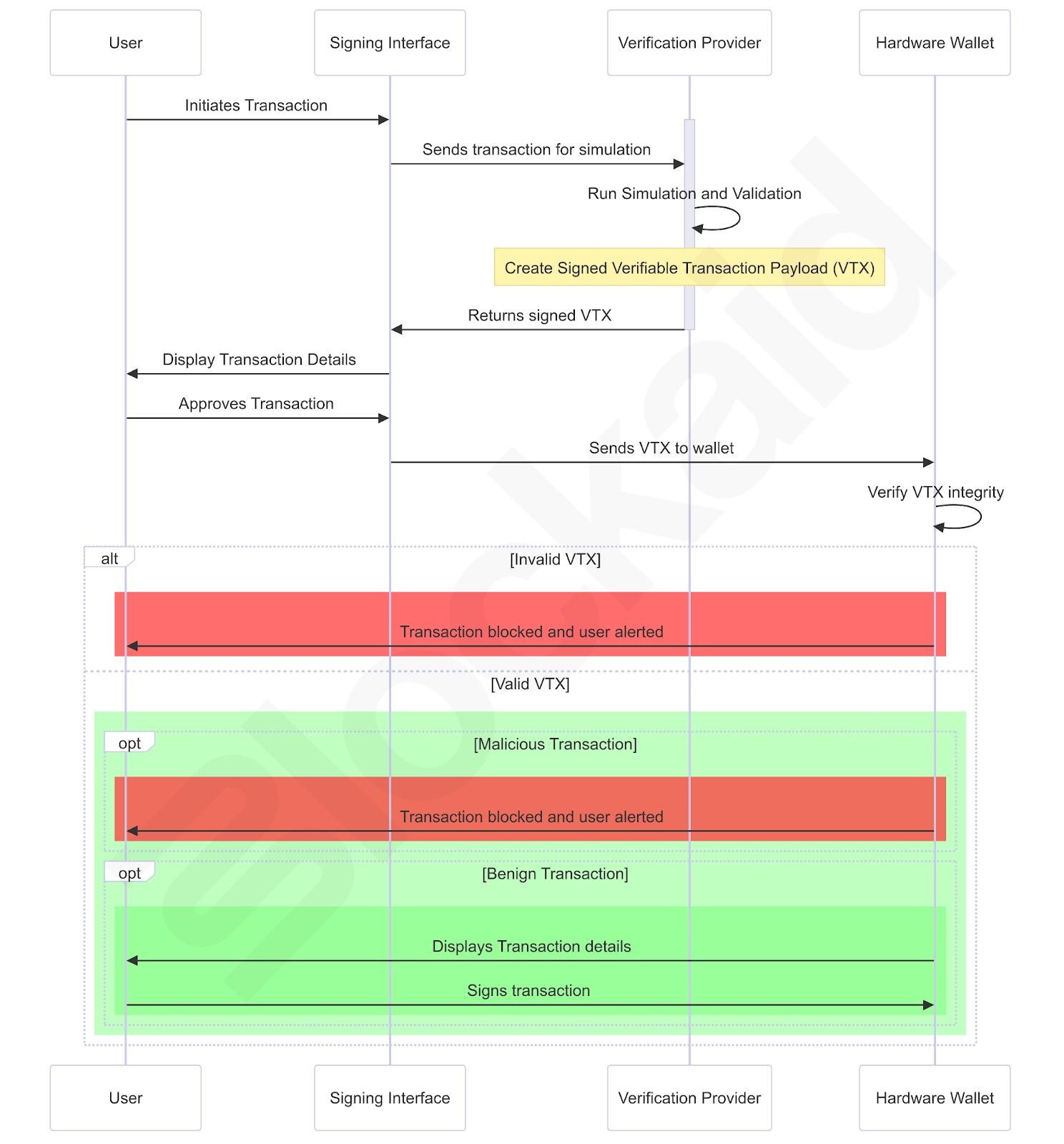
- The signing interface sends the transaction to the verification provider:
- When the user initiates a transaction, the signing interface sends the transaction data to the verification provider for further processing.
- Simulation and validation by the verification provider:
- The verification provider runs a simulation of the transaction to predict its behavior and ensure it matches the user’s intent. This simulation highlights any unexpected outcomes or risks.
- Next, the provider performs validation, analyzing the transaction to assess if it is potentially malicious or harmful to the user.
- The verification provider then generates a verifiable transaction payload (VTX), which contains all three pieces - the transaction, the simulation result, and the validation result.
- Cryptographic signing of the VTX:
- With the VTX ready, the verification provider cryptographically signs the payload. This signature ensures that the transaction, simulation, and validation results have not been altered and remain secure from tampering.
- The signed VTX is then sent back to the signing interface, where the user reviews and details (based on the simulation and validation result)
- Once the user accepts the transaction, it is sent to the hardware wallet for final verification and signing.
- Hardware wallet verifies the VTX:
- Upon receiving the VTX, the hardware wallet verifies its integrity by checking the cryptographic signature using the public key of the verification provider.
- This verification ensures that the transaction has not been tampered with during transmission.
- If the signature does not match, the hardware wallet alerts the user and marks the transaction as untrustworthy.
- Final transaction signing:
- Once the signature is verified, the hardware wallet has complete confidence that the transaction matches the simulation and validation results. It can now:some text
- Present an accurate preview of the transaction to the user, knowing that the simulation accurately reflects the transaction.
- Reference the validation result to detect whether the transaction is malicious, warning the user if necessary.
- These capabilities allow the user to make sure that the transaction they sign is the same one they’ve seen in the signing interface - and that it is benign and favorable.
- The user can then sign the transaction, fully assured that it has not been altered and has been validated for safety.
Overview of the transaction verification architecture
How transaction verification protects against a compromised signing interface
The VTX plays a crucial role in protecting against attacks where the signing interface is compromised. Even if the signing interface displays a legitimate transaction while secretly sending a different, malicious transaction to the hardware wallet, the cryptographically signed VTX ensures security.
Because the hardware wallet verifies the VTX on its own, it no longer needs to rely entirely on the signing interface for security.
The wallet can independently validate that the transaction matches the simulation and that the validation results confirm the transaction is safe.
If any part of the transaction has been altered, the signature verification will fail, alerting the hardware wallet and preventing a malicious transaction from being signed.
This independence ensures that even in the event of a compromised signing interface, users are protected from blindly signing a harmful transaction.
Key benefits of transaction verification
- End-to-end security: By cryptographically verifying the transaction from simulation to signing, transaction verification ensures that no tampering occurs at any stage of the process.
- Accurate transaction preview: The hardware wallet can confidently present an accurate transaction preview, knowing that the simulation matches the real transaction without needing to perform its own simulations.
- Tamper detection: If any part of the transaction is modified between the signing interface and the hardware wallet, the cryptographic signature verification will fail, alerting the user to the potential risk.
- No additional computational burden: The hardware wallet can perform verification without needing extra computational resources or network access, preserving its security guarantees.
Implementation of transaction verification
Integrating transaction verification into the current transaction signing ecosystem requires a seamless approach that preserves the core security principles of hardware wallets while adding an essential layer of cryptographic verification.
The implementation focuses on minimal overhead, high compatibility with existing hardware wallets, and ease of integration with signing interfaces.
Integration with signing interfaces
The first step in implementing transaction verification is adapting the signing interfaces—software wallets, dApps, or other transaction-signing platforms—to work with the verification provider.
- Transaction submission:
- When a user initiates a transaction, the signing interface sends the transaction data to the verification provider instead of directly communicating with the hardware wallet.
- Verification process:
- The verification provider then performs the simulation and validation of the transaction as described earlier, bundling the results into a Verifiable Transaction Payload (VTX).
- VTX delivery to the hardware wallet:
- Once the VTX is generated and cryptographically signed, the signing interface forwards the VTX to the hardware wallet for verification and final signing.
The signing interface itself doesn’t require heavy modifications beyond routing transaction data through the verification provider. This ensures that users can continue using their familiar signing workflows, with added security in the background.
Creating verification providers
To implement transaction verification, building verification providers is essential. These providers will handle the core processes of simulating, validating, and signing transactions before they reach hardware wallets. Here’s what needs to be considered when creating these providers:
- Fast and accurate simulation and validation: The provider must process transaction simulations and validations quickly and accurately to ensure a smooth user experience. Handling large volumes of transactions in real time is crucial to avoid adding friction to the signing process.
- Security-first architecture: The verification provider must be built with a security-first mindset, ensuring the protection of cryptographic keys and sensitive transaction data. Teams creating these providers need expertise in cybersecurity and Web3 security to anticipate threats from both traditional and decentralized systems. This means implementing strong encryption, secure key management, and a robust infrastructure that prevents tampering and unauthorized access.
- Seamless integration with ecosystems: The verification provider should integrate easily into existing hardware wallets and signing interfaces, requiring minimal changes. Simple firmware updates should allow hardware wallets to verify the cryptographic signatures, and signing interfaces should be able to route transactions to the provider with minor adjustments. This ensures the provider can be widely adopted without causing disruptions to existing workflows.
By focusing on these three areas—speed, security, and integration—creating verification providers becomes a critical step in rolling out transaction verification successfully. These providers enable users to trust that their transactions are properly simulated, validated, and securely signed before finalizing them on the hardware wallet.
Hardware wallet adaptation
Hardware wallets will need a lightweight firmware update to handle the verification and processing of the VTX, with minimal impact on existing functionality.
- Signature verification:
- The hardware wallet must be able to verify the cryptographic signature of the VTX using the public key of the verification provider. This ensures that the VTX has not been tampered with during transmission from the signing interface to the hardware wallet.
- Since hardware wallets, by their very nature, include both the hardware and software components required for cryptographic operations, adding this step will not require any new library code or hardware.
- Transaction parsing and display:
- Once the signature is validated, the hardware wallet parses the VTX to extract the transaction, simulation results, and validation. The wallet can then display the verified transaction details to the user, offering an accurate preview of what they are about to sign.
- Validation result handling:
- The hardware wallet uses the validation result within the VTX to determine if the transaction is safe or malicious. If the validation result indicates malicious activity, the wallet will alert the user, preventing the signing of harmful transactions.
- Final transaction signing:
- After verifying the VTX and confirming the transaction’s safety, the hardware wallet enables the user to sign the transaction, ensuring it matches the simulation and validation results.
Recap
As the Web3 ecosystem continues to grow, so do the complexities and risks associated with transaction security.
Hardware wallets have traditionally focused on key management, leaving the verification of transaction details to signing interfaces. This creates a critical gap, where users often approve transactions without being certain of what they are signing—a vulnerability exploited by attackers in incidents like the Radiant Capital breach.
Transaction verification solves this problem by introducing an additional layer of security that ensures users are signing exactly what they intend.
- Through the use of verification providers, transactions are simulated and validated before being sent to the hardware wallet.
- The result of this process is a verifiable transaction payload (VTX)—a cryptographically signed bundle that contains the transaction, its simulation, and validation results.
- The VTX enables hardware wallets to independently verify the transaction’s integrity without relying solely on the signing interface, which can be compromised.
- By checking the VTX’s cryptographic signature, the hardware wallet confirms that the transaction has not been tampered with and that the user is signing what was originally validated.
This solution prevents blind signing, and helps ensure that the user sees and approves a fully validated and verified transaction before it is signed.
About Blockaid
As the leading onchain security platform, Blockaid is committed to solving these transaction security challenges. This is why we are working to create a verification provider that checks all the critical requirements:
- Fast and accurate simulations and validations, the same ones powering the leading software wallets, like Coinbase Wallet, Metamask, Zerion, and more.
- A security-first design built by our team of cybersecurity and onchain security experts, ensuring that all threat vectors are covered and taken into consideration.
- Seamless integration with every company that already works with Blockaid, ensuring widespread availability from day one.
We recognize that blind signing is an industry-wide issue that affects the entire Web3 ecosystem. That’s why we are releasing this whitepaper—not just to showcase our solution but to encourage broader industry efforts in addressing this critical problem.
We believe that, together, the community can take meaningful steps to make transaction signing as secure as possible.
Blockaid invites hardware wallet manufacturers, protocol developers, and anyone interested in improving Web3 transaction security to collaborate with us.
If you’re a hardware wallet provider looking to implement transaction verification, or a protocol developer aiming to integrate this system, we would love to connect.
Let’s work together to secure the next generation of decentralized applications and build a safer, more trusted Web3 ecosystem.
Blockaid is securing the biggest companies operating onchain
Get in touch to learn how Blockaid helps teams secure their infrastructure, operations, and users.




