Threat Report: AngelX

On August 29, Blockaid Threat Intel team became aware of a new drainer variant being tested in the wild.
This drainer was detected by our systems during regular proactive scans of newly deployed dApps - allowing us to catch a test dApp, that was likely never meant to be viewed by anyone other than the drainer developers.
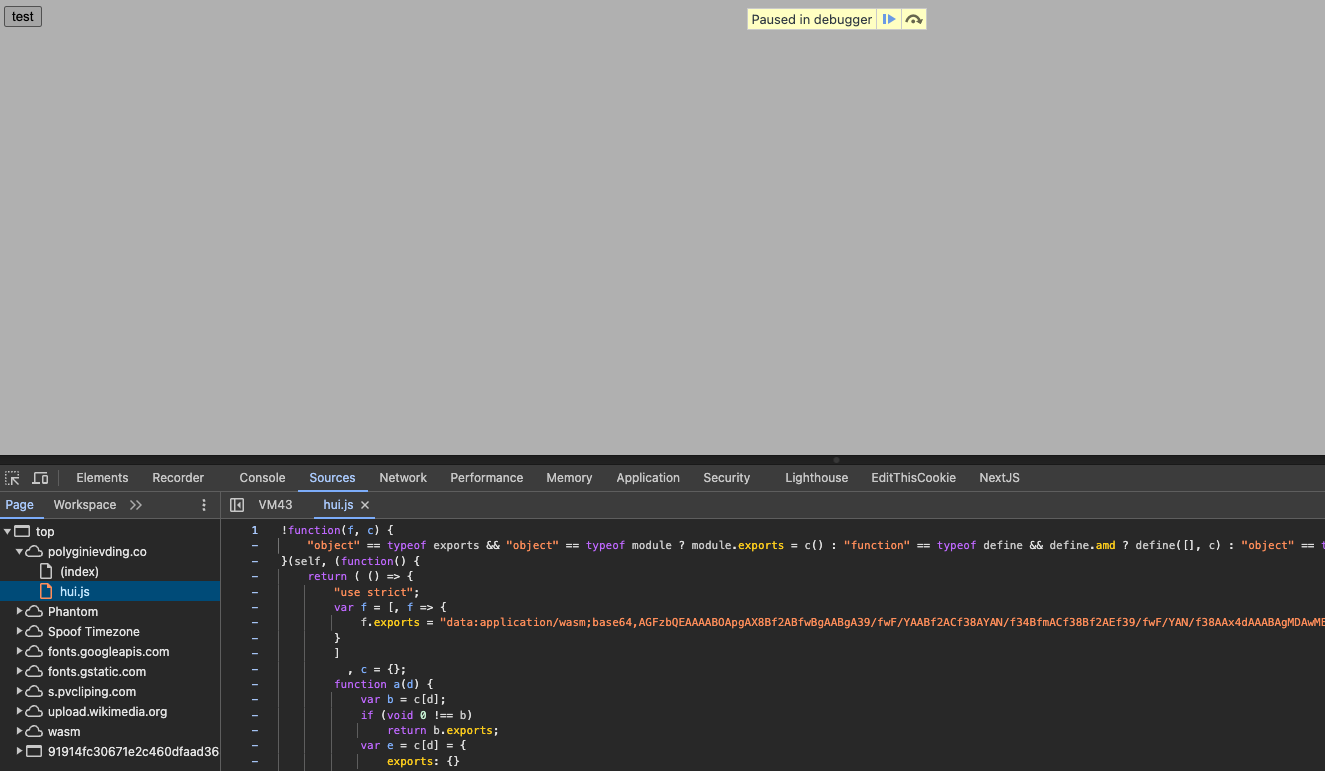
While our systems successfully detected this test dApp as malicious, it contained a sample of a new, unknown drainer variant.
After additional research, we were able to procure additional samples, which allowed us to identify this as a new, yet to be released variant of Angel Drainer.
AngelX
This suspicion was confirmed on September 1st, when Angel Drainer announced on their Telegram channel that they are releasing a new version of their toolkit, dubbed AngelX.
According to Angel, this new version was unique as it included major improvements that were made in order to make new malicious dApp deployment much easier. Among these new features:
- Support for draining users on new, previously unsupported chains - including TON and TRON.
- A new command and control (CNC) dashboard for scammers, giving them a high level of control over how they conduct their scams.
- Support for a seed-phrase-theft flow
- New cloaking mechanism, meant to prevent detection by security vendors
On top of the samples, our team was able to gain access to the control panel of an AngleX instance, allowing us to examine the different ways Angel is working to improve the ease of drain:
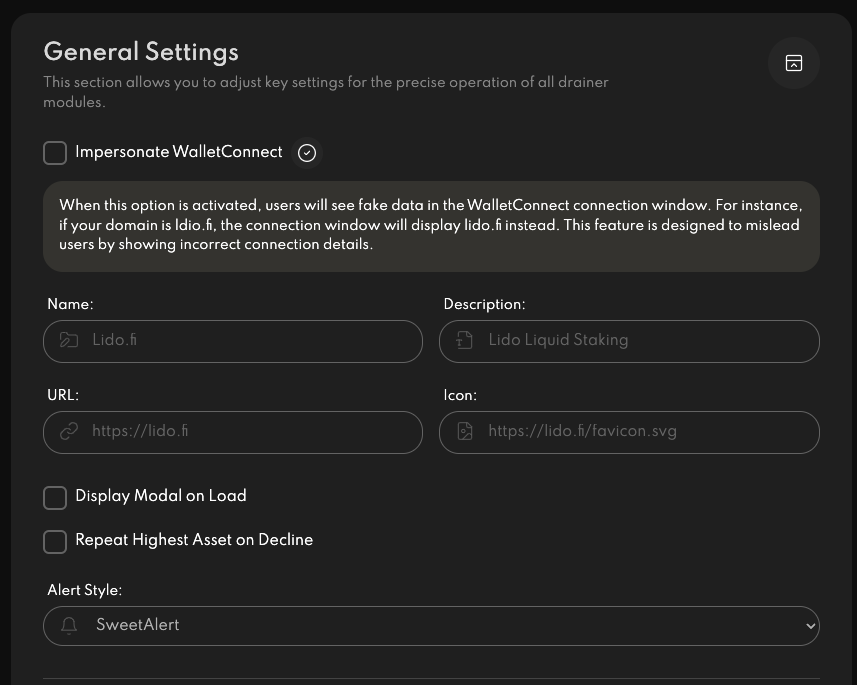
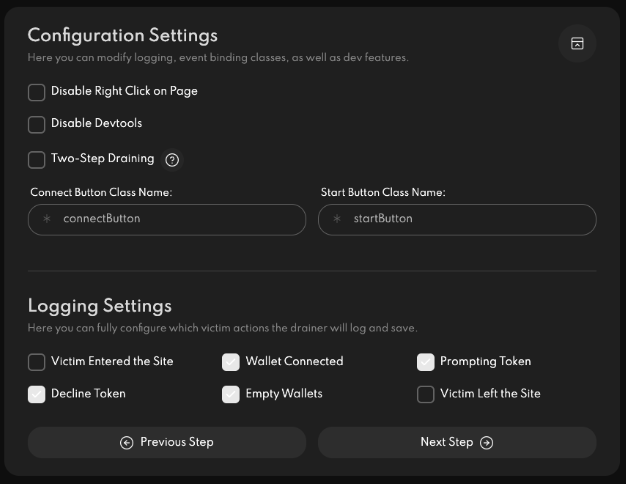
Mitigation
As Blockaid Threat Hunting team was able to secure samples of this new variant ahead of its release to scammers, we were able to mitigate Angel’s bypass attempts and add detection logic before the drainer was released to scammers.
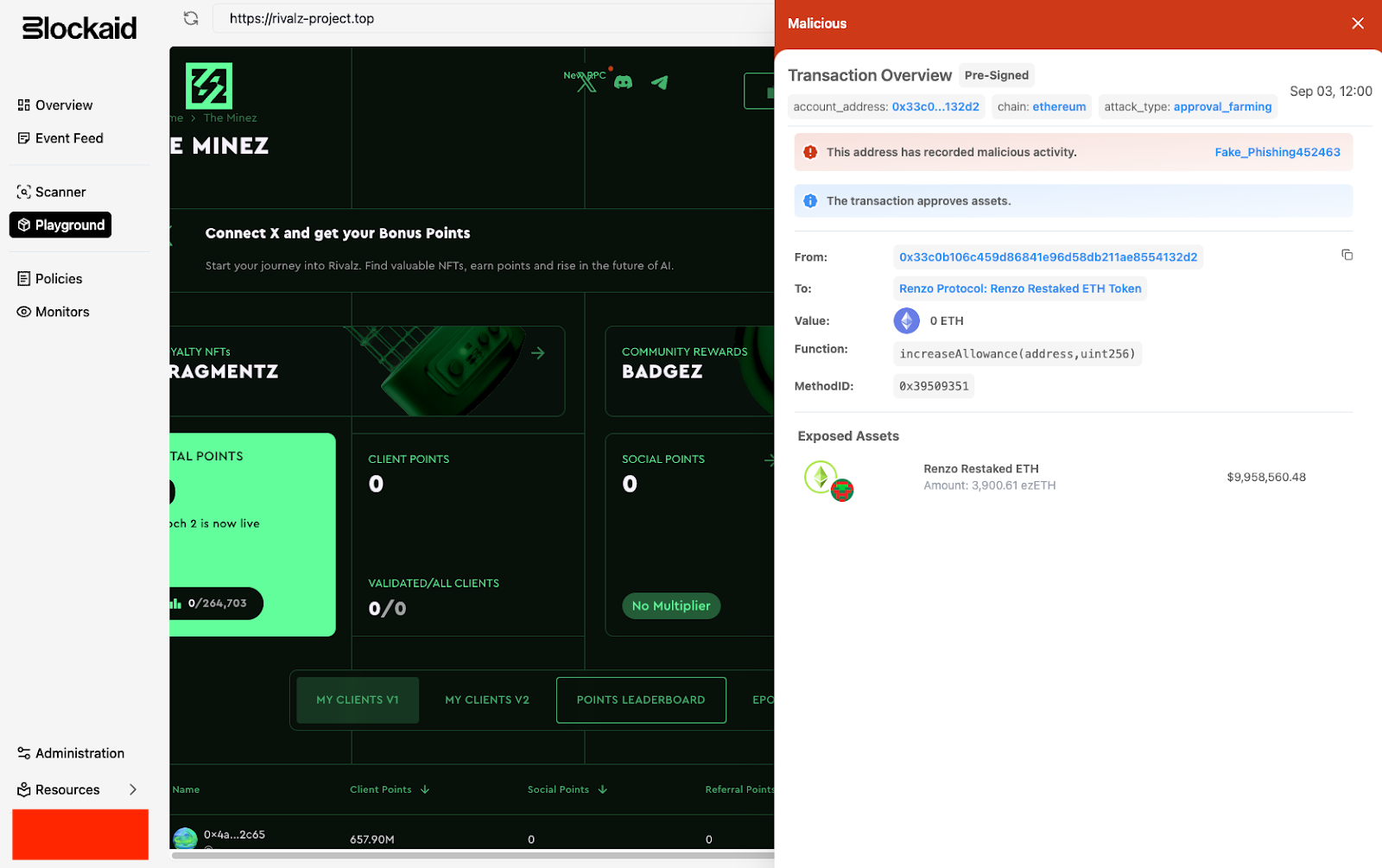
As you can see in the chart below, this pre-release effort proved highly valuable, with an explosive growth in Angel-powered scams starting with the release of the new variant:
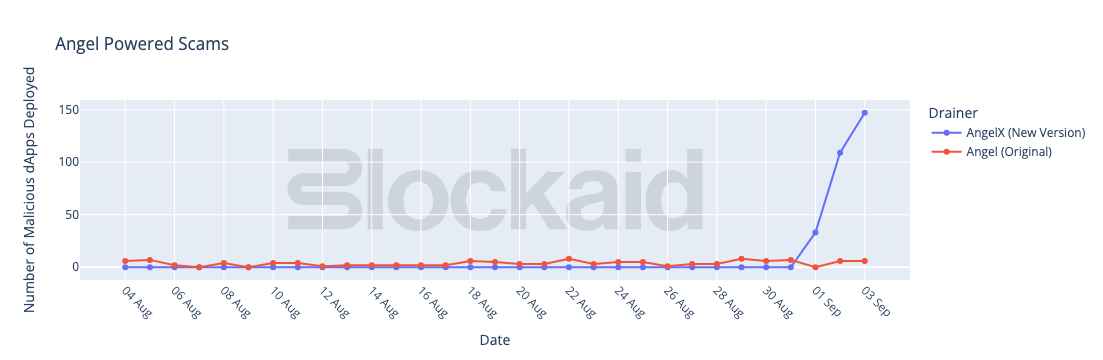
Conclusion
This incident is another example of how proactive monitoring and early intervention are crucial in today’s adversarial Web3.
By catching the AngelX drainer variant during its testing phase, our team could develop and implement defenses before it became widely used.
This early action underscores how critical it is to monitor for evolving threats, especially as attackers continuously adapt their methods to target new platforms and users.
Blockaid is securing the biggest companies operating onchain
Get in touch to learn how Blockaid helps teams secure their infrastructure, operations, and users.




