The $230M Blind Spot: Lessons from the WazirX Hack

On July 18th, 2024, hackers stole $230 million in assets from cryptocurrency exchange WazirX.
In the weeks following the attack, we spoke to dozens of web3 companies about what happened. There was one major blind spot everyone seemed to miss.
Blind signing transactions.
Here’s what happened, an overview of blind signing, and how you can protect against this kind of attack.
How the WazirX hack worked
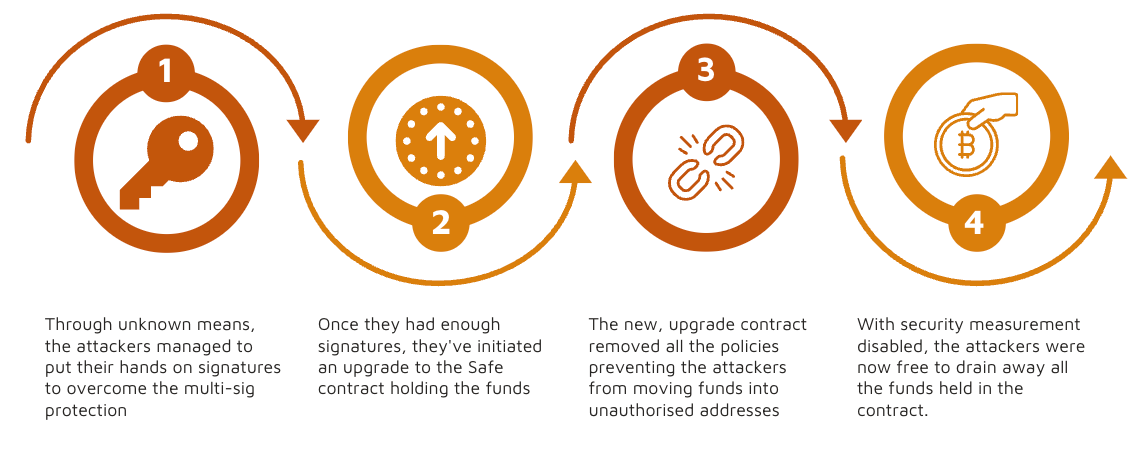
There are still quite a few unknowns but it boils down to this: attackers were able to get enough signatures to upgrade the Gnosis safe, transfer funds to the new safe, and then drain $230m in assets.
WazirX security measures
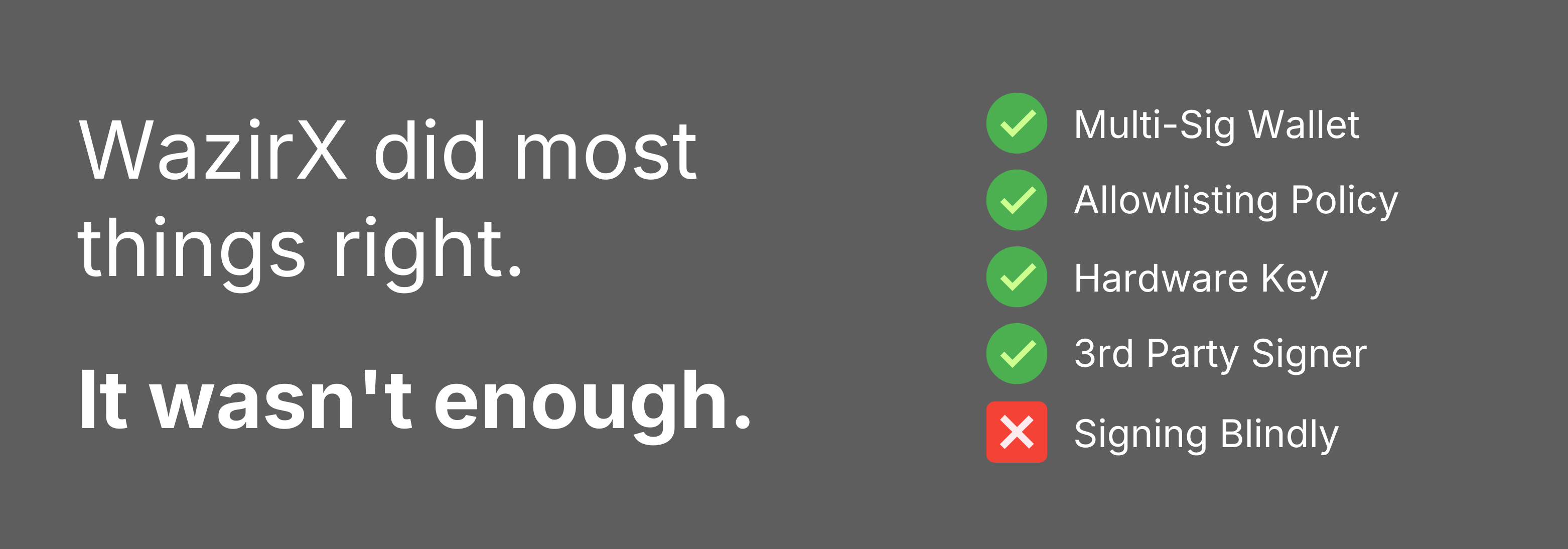
From a security standpoint, there were a lot of things that WazirX did well. The wallet operated under a complex security structure that included:
- Multisig wallet with Gnosis Safe
- Whitelisted addresses through Liminal
- Ledger hardware wallets for WazirX signatories
- Liminal signatory approval
We don’t know exactly how the hackers gained access, but we do know that upgrading the safe required three signatures from Gnosis and one from Liminal—and that those signatures were blind signed.
How blind signing works
Picture this: You're handed a document in a sealed envelope. You're told it's routine, so you sign without opening it. Now imagine that document just cost your company $230 million.
That's essentially what happened to WazirX. Signers couldn't see the full details of what they were signing but trusted the transaction was safe to sign.
Why? The transaction was cleverly designed to look legitimate by exploiting a limitation in ERC20 transactions where hardware wallets don’t display full details.
Signing a transaction without seeing the full details is known as blind signing, and it’s actually a more common practice than it should be.
Protecting against blind signing
Transaction signing is the single largest attack surface in web3. That’s why transaction-level security is one of the most important pieces in the security stack.
At the very minimum, transaction-level security should include policies prohibiting blind signing, full transaction details at any point of signing, and transaction simulation and validation.
With transaction simulation, you reduce the risk of signing a transaction that produces a different outcome than represented. Outcomes like transferring more assets than intended or modifying contract states and permissions.
However, simulation alone isn’t enough. Attacks often add additional actions that aren’t reflected in onchain changes. This is where transaction validation comes in.
Transaction validation examines the security ramifications of the onchain state changes to detect any second or third-degree risks that are introduced by the transaction outcomes.
Things like:
- Which actors are now in control of your assets?
- Are these actors trustworthy?
- Does the contract you’ve just deposited your funds into contain malicious code that will prevent you from withdrawing?
Think about it like this:
- Simulation protects you from sending one million dollars when you meant to send $100.
- Validation protects you from sending $100 to a North Korean hacker impersonating a new airdrop campaign.
Summary
WazirX should be a wake-up call for the industry. You can have all sorts of security measures and still be vulnerable to malicious transactions.
To protect yourself and your users:
- Prohibit blind signing
- Ensure mission-critical transactions display the full details
- Implement transaction simulation to understand what will happen onchain
- Implement transaction validation to determine if a transaction is safe
Blockaid is securing the biggest companies operating onchain
Get in touch to learn how Blockaid helps teams secure their infrastructure, operations, and users.




