Squarespace Domain Hijacking Incident: Attack Report

Last week, a couple of major DeFi protocol frontends were hacked. At first, these incidents seemed unrelated - just another day in the volatile world of Web3 security. However, as the dust settled, a disturbing pattern emerged. These attacks were all linked - a result of a large-scale domain hijacking campaign targeting Squarespace users, a popular web building and hosting platform.
This unprecedented attack sent shockwaves through the crypto community, blurring the lines between traditional cybersecurity and blockchain protection. As the crypto world grappled with the fallout, one thing became crystal clear: in our interconnected digital landscape, vulnerabilities in conventional web infrastructure can have catastrophic consequences for decentralized applications and their users.
In this post, we'll dive deep into the Squarespace domain hijacking incident, exploring how it happened, why it was so devastating, and what it means for the future of Web3 security. More importantly, we'll discuss why this incident serves as a wake-up call for the entire industry, highlighting the urgent need for more comprehensive, proactive security measures that bridge the gap between Web2 and Web3.
Background: When Web2 Vulnerabilities Become Web3 Nightmares
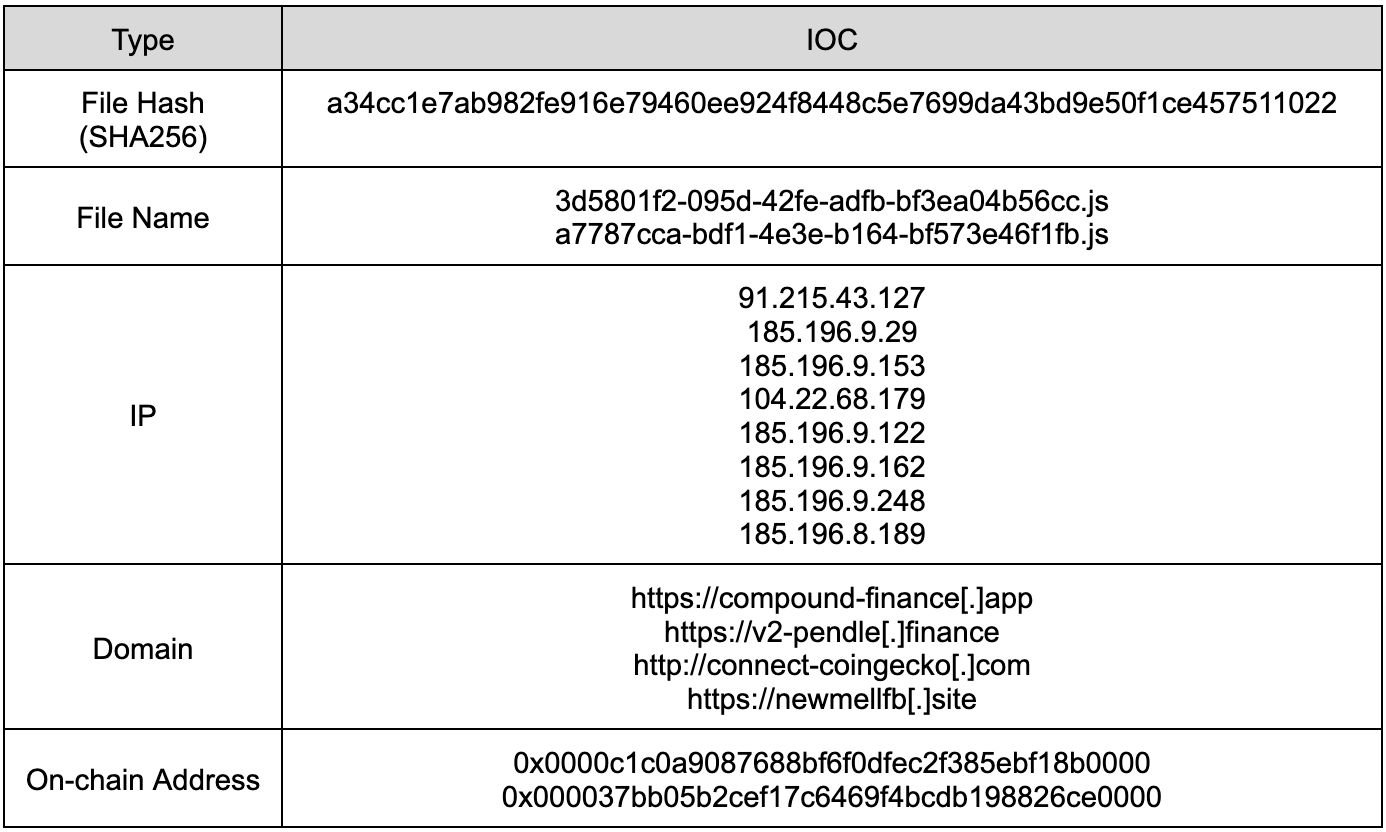
The attack first came to light when Ethereum-based DeFi protocol Compound and multi-chain interoperability protocol Celer Network reported that their front-ends were compromised. Visitors to these sites were being redirected to malicious pages designed to drain funds from connected wallets. As more protocols fell victim, with yield protocol PendleFi also breached, the community began to suspect a larger, coordinated attack.
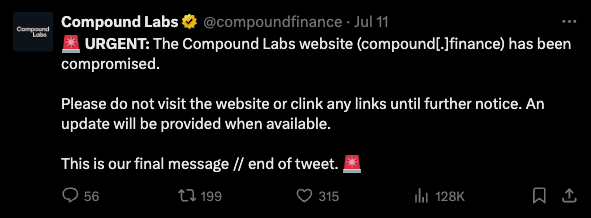
After inspecting the affected projects, a common thread was found: all affected sites used Squarespace for domain management. Further investigation revealed that attackers were manipulating DNS A Records, redirecting users to malicious dApps that perfectly mimicked the original sites. These fake dApps were running the latest iteration of the Inferno draining kit, designed to trick users into signing transactions that would empty their wallets.
Why It Happened
After more research, the community was able to conclude that the root of the attack was indeed Squarespace - or, rather, Squarespace's acquisition of Google Domains in 2023. During the migration of millions of domain registrations to Squarespace, a critical security oversight occurred: two-factor authentication (2FA) was disabled for all migrated accounts, including those that previously had it enabled. This created a significant vulnerability across a vast number of domains seemingly overnight.
Attackers exploited this security gap using a technique called password spraying. Unlike traditional brute-force attacks that try many passwords on a single account, password spraying attempts a small number of commonly used passwords across a large number of accounts. This method is particularly effective because:
- It's less likely to trigger account lockouts or alert security systems, as it doesn't bombard a single account with attempts.
- It exploits the unfortunate reality that many people use weak, common passwords across multiple accounts.
- It can be automated to work at scale, allowing attackers to attempt access on thousands or even millions of accounts relatively quickly.
In this case, with 2FA disabled during the migration, password spraying became even more potent. Normally, even if an attacker guessed a correct password, they'd be stopped by the second authentication factor. Without this extra layer of security, a correct password guess immediately granted access to the account.
This combination of factors - the large-scale migration, the temporary removal of 2FA, and the efficient password spraying technique - created a perfect storm. It allowed the attackers to compromise numerous Squarespace accounts simultaneously, explaining why so many apparently unrelated sites were affected at once.
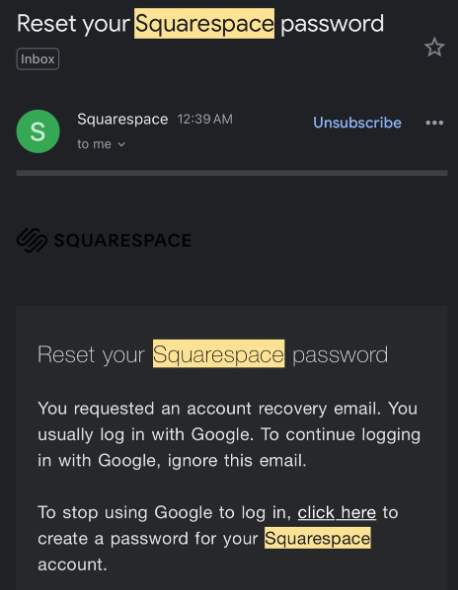
Example of an email sent to @samwcyo alerting them to a password reset attempt
The Attackers' Modus Operandi: A Deep Dive
Once the attackers gained access to Squarespace accounts through password spraying, they executed a sophisticated plan to compromise DeFi protocols and their users. Here's a step-by-step breakdown of their modus operandi:
- Account Takeover: After successfully guessing passwords, the attackers gained control of Squarespace accounts associated with high-value DeFi protocols.
- Malicious dApp Creation: The attackers then created impersonating malicious decentralized applications (dApps) that closely mimicked the branding and interface of the targeted DeFi sites.
- DNS Record Manipulation: In a critical step, the attackers changed the DNS records of the compromised sites. They pointed the domain names to their malicious dApps instead of the legitimate sites.
- User Redirection: As a result, users who entered the correct, legitimate URLs in their browsers were unknowingly redirected to the malicious dApps. From the users' perspective, everything appeared normal - they were on the correct domain, with familiar branding.
- Malicious Transactions: Once on the fake site, users were prompted to connect their wallets and perform transactions. These transactions, however, were designed to drain funds or grant the attackers access to the users' assets.
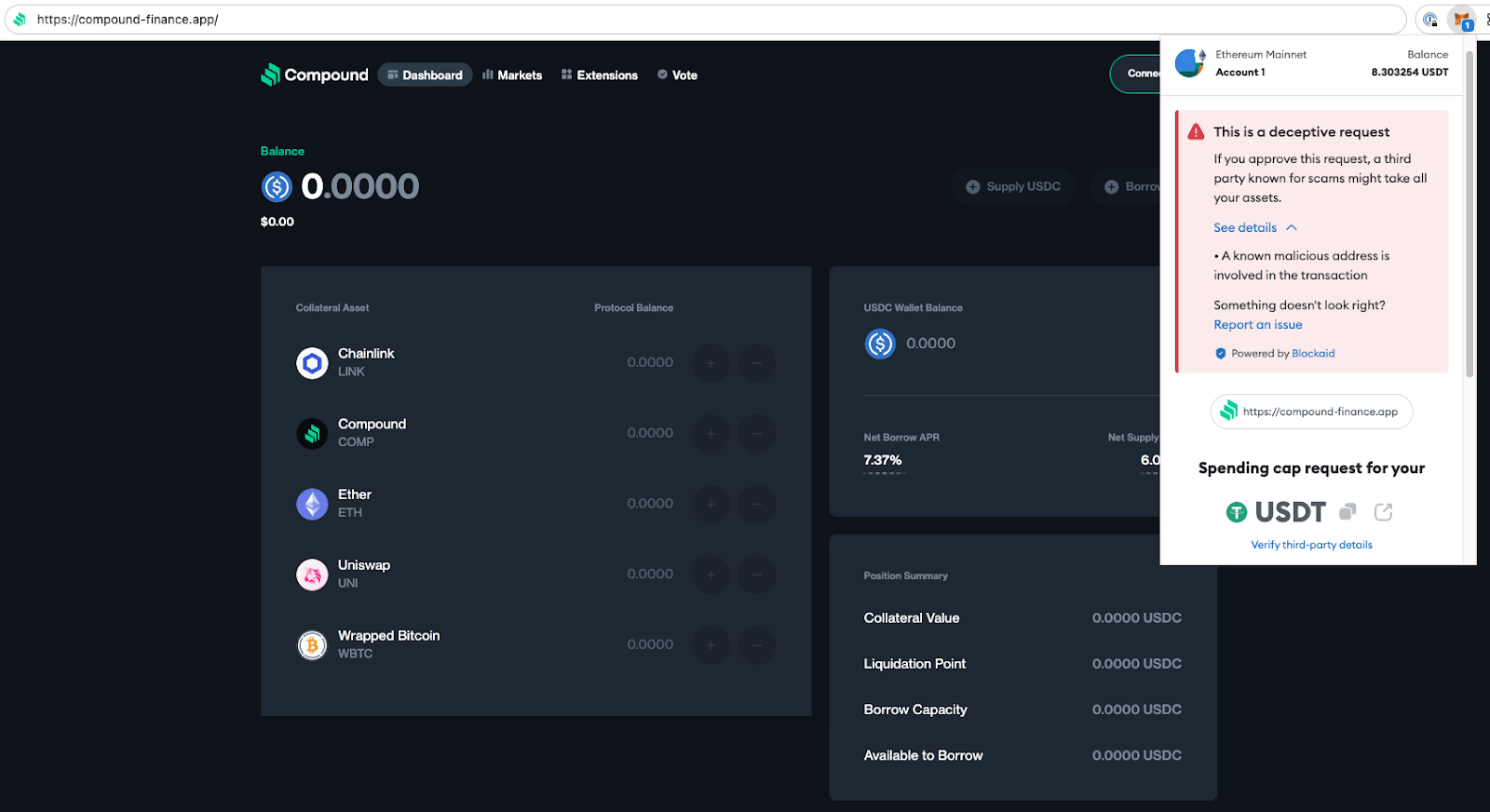
This pattern of attack - from account takeover to DNS manipulation to user redirection and finally to malicious transactions - was seen repeating itself on every one of the attacked dApps. At Blockaid, we've observed attempts to execute the same attack pattern against some of our customers. Thanks to our proactive security measures, we were able to successfully block these attempts, protecting users of our customers from potential losses.
Unraveling the Attack
As the attacks unfolded, Blockaid's Threat Intelligence team sprung into action, leveraging our extensive network and advanced analytics to piece together the puzzle. Our unique position in the Web3 security landscape allowed us to quickly identify and confirm the connections between what initially appeared to be isolated incidents.
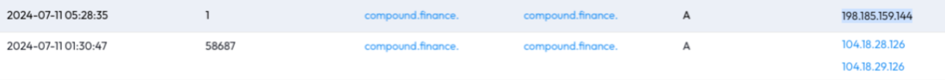
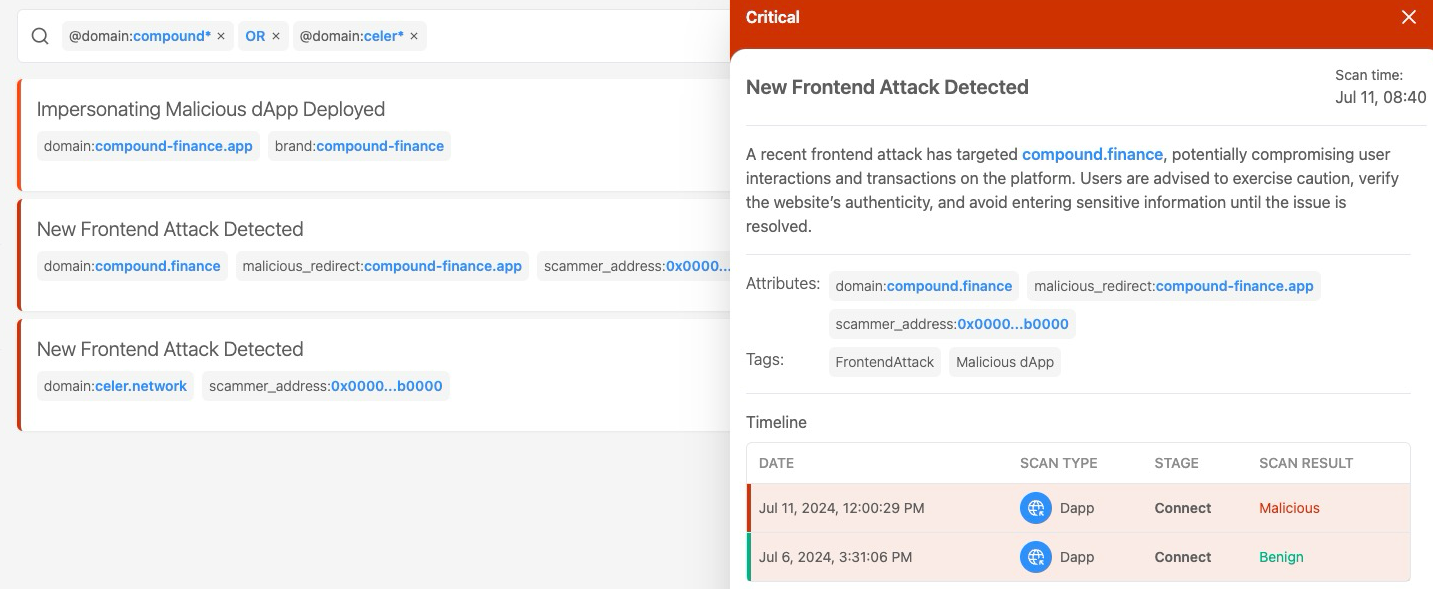
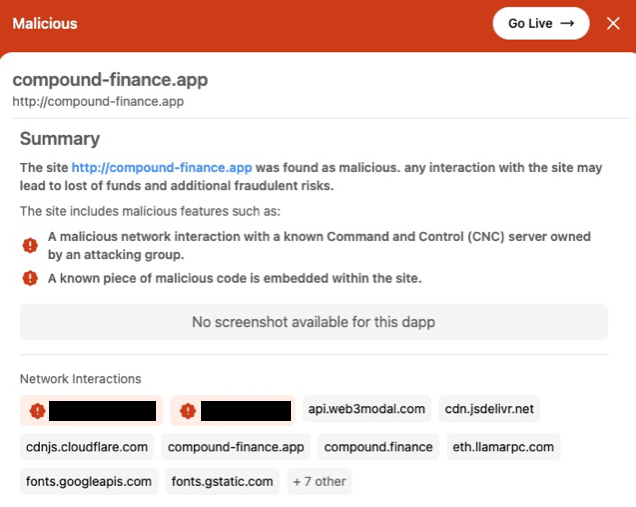
Using data from the Blockaid network, our team identified a critical commonality across multiple compromised sites: they were all using the same malicious Drainer SDK. This discovery was the key that unlocked our understanding of the attack's true scope and sophistication.
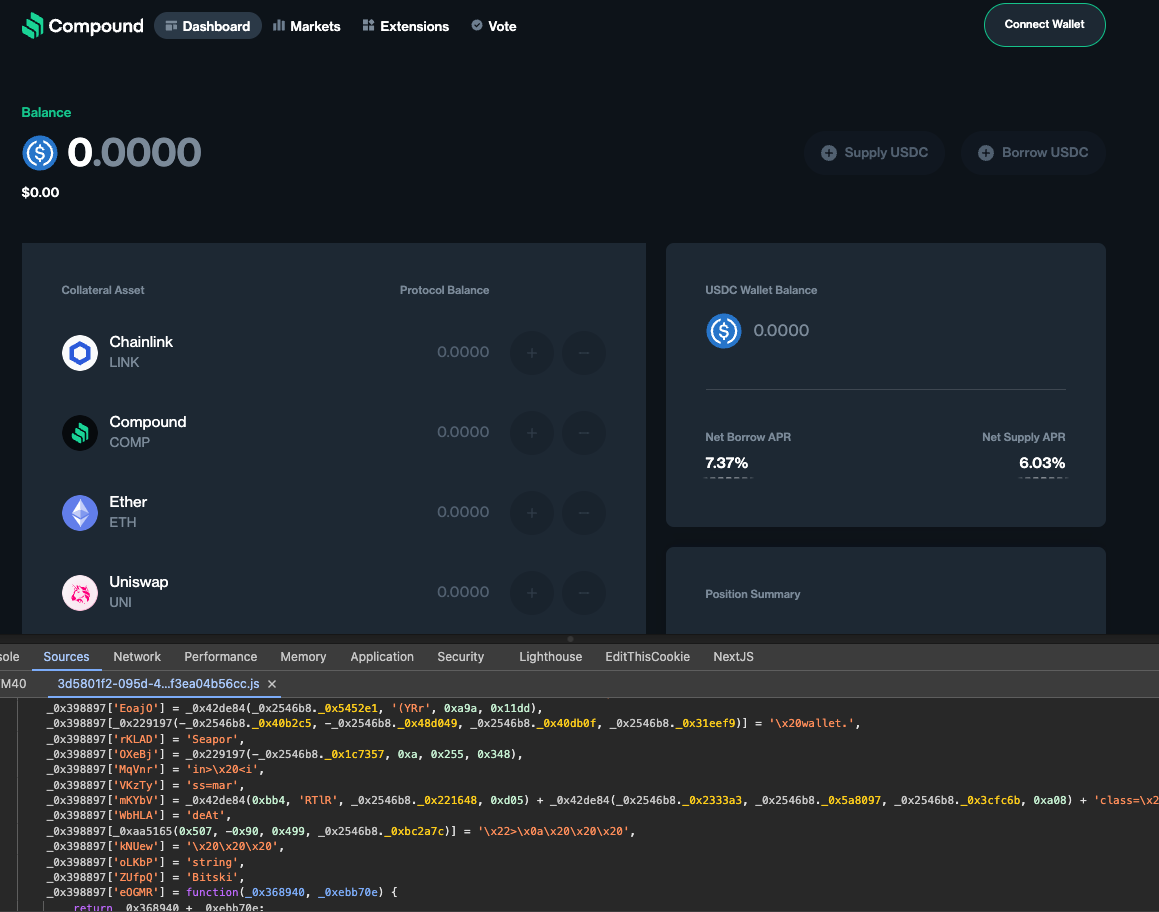
With this insight, we conducted a reverse search on files used by the identified Drainer SDK. This process led us to uncover numerous dormant malicious dApps that had not yet been activated. Surprisingly, many of these dApps were hosted on the same provider (some even on the same server), revealing a centralized infrastructure behind the seemingly decentralized attacks.
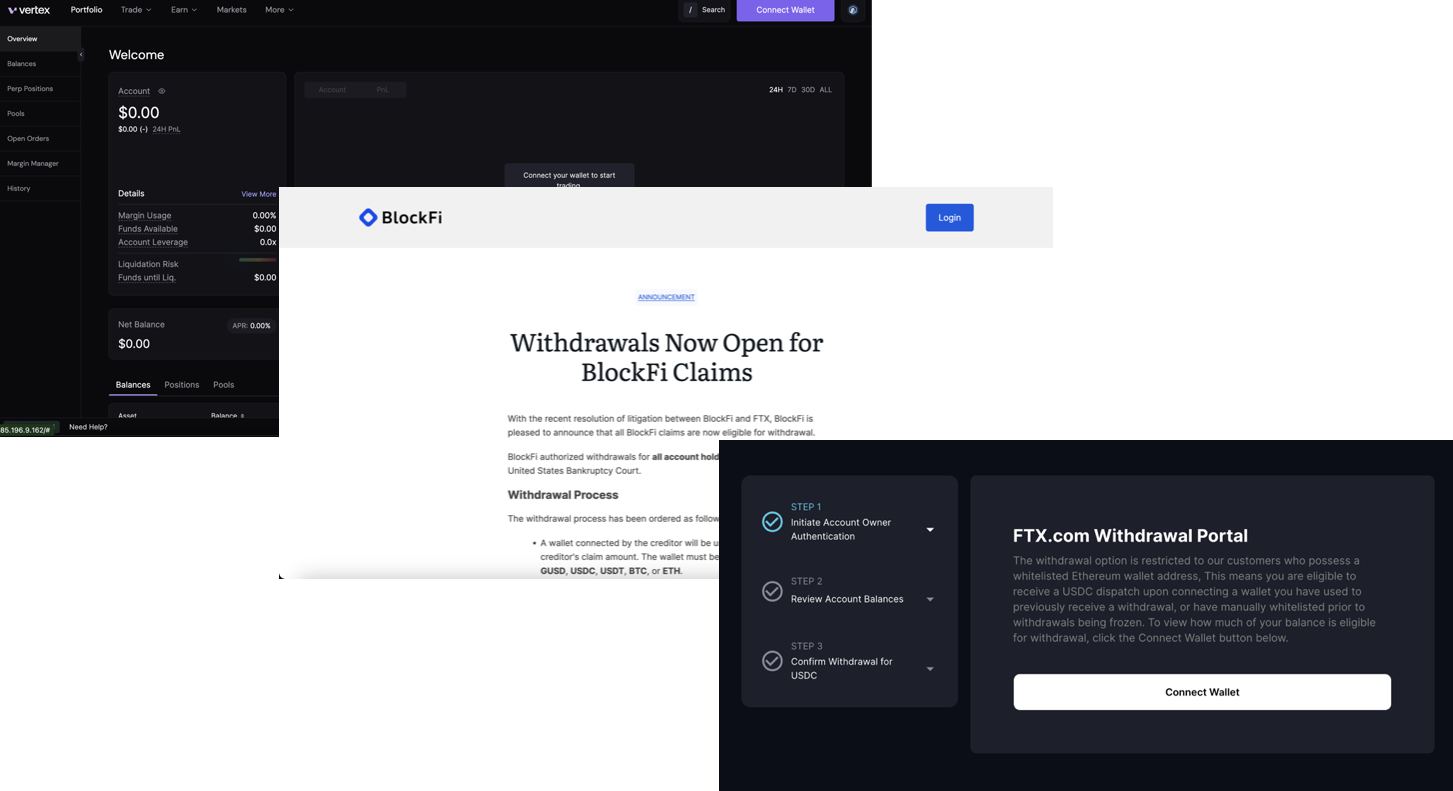
Dormant malicious dApps deployed by the attackers
This finding not only confirmed that the attacks were indeed tied together but also gave us a proactive edge. By identifying these dormant threats, we were able to flag them before they could be activated, potentially preventing future attacks.
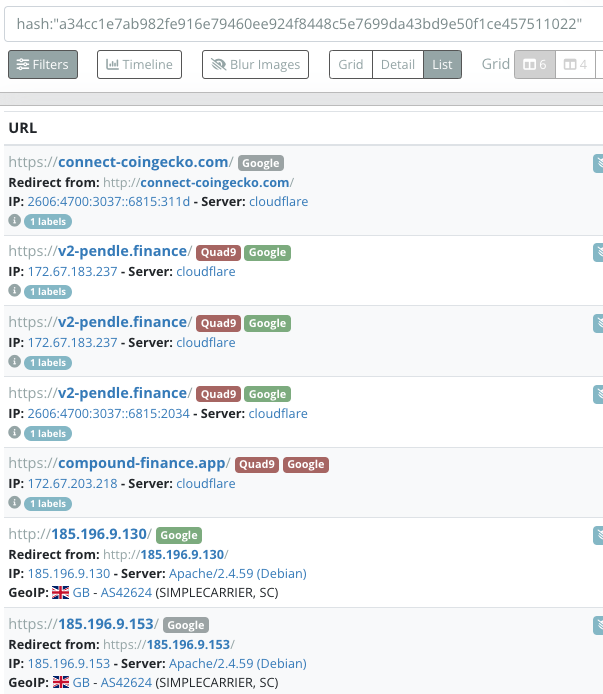
Taking our investigation a step further, we reached out to the hosting provider to request additional details. This proactive approach aims to gather more information about the attacker's infrastructure and potentially aid in shutting down their operations.
A Wake-Up Call: Rethinking Web3 Security
The Squarespace domain hijacking incident serves as a stark wake-up call for the entire Web3 ecosystem. It exposes critical vulnerabilities in our current security paradigms and underscores the need for a more comprehensive, multi-layered approach to protecting decentralized applications and their users.
Blocklists Are Not Enough
This attack is a powerful reminder that even legitimate, trusted sites can be compromised. Relying solely on blocklists of known malicious sites is no longer sufficient. The attackers in this case exploited trusted domains, rendering traditional blocklists ineffective. We must shift our security mindset from simply avoiding known threats to actively verifying the integrity of every interaction.
The Need for Proactive Monitoring
The incident highlights the critical importance of proactive monitoring. It's not enough to assume that a site is safe because it was secure yesterday. Continuous, real-time monitoring is essential to detect when legitimate sites are compromised. This approach allows for rapid response to emerging threats, potentially preventing or minimizing damage from attacks like this one.
Beyond dApp Scanning: The Importance of Transaction Scanning
While dApp scanning is a crucial security measure, this attack demonstrates that it's not sufficient on its own. Implementing transaction scanning provides an additional, critical layer of security. By analyzing each transaction in real-time, regardless of the perceived legitimacy of the dApp, we can catch malicious actions that might slip through other security layers. This "defense in depth" strategy is essential in an ecosystem where the lines between legitimate and malicious can blur in an instant.
Conclusion
As the attack unfolded, Blockaid was at the forefront of monitoring and responding to the situation in real-time. Our team's expertise and advanced security systems played a crucial role in mitigating the impact of this widespread attack, helping our targeted customers to keep their platforms secured and their users safe.
Immediate Monitoring and Assistance
From the moment the first signs of the attack emerged, Blockaid's threat intelligence team was actively tracking the situation. We provided immediate assistance not only to our existing customers but also extended our support to non-customers who found themselves targeted by this sophisticated attack. This rapid response helped numerous projects secure their infrastructure and protect their users during this critical time.
Proactive dApp Scanning in Action
Our proactive dApp scanning systems proved invaluable in this crisis. These systems were able to quickly detect anomalies in the behavior and structure of compromised dApps, alerting us to the attack even before many projects realized they had been compromised. This early warning system allowed us to take swift action and notify affected parties, potentially preventing significant losses.
Threat Intelligence and Infrastructure Mapping
Blockaid's threat intelligence team demonstrated their expertise by rapidly detecting the DNS changes that were central to this attack. This crucial insight allowed us to map out the entire infrastructure being used by the attackers. By understanding the full scope of the attack, we were able to:
- Identify other potential targets before they were compromised
- Provide detailed threat intelligence to security partners and law enforcement
- Develop and implement targeted countermeasures to protect against similar attacks in the future
Leveraging Insights for Enhanced Protection
The insights gained from this incident have been invaluable in further refining our security measures. We've enhanced our monitoring systems, improved our dApp scanning algorithms, and strengthened our transaction analysis capabilities. These improvements ensure that Blockaid remains at the cutting edge of Web3 security, ready to defend against both current and emerging threats.
This incident underscores the critical importance of proactive, multi-layered security in the Web3 space. At Blockaid, we remain committed to staying one step ahead of potential threats, continuously innovating our security solutions to protect the decentralized ecosystem and its users. As the Web3 landscape evolves, so too will our defenses, ensuring that we continue to provide the highest level of security for our clients and the broader community.
Blockaid is securing the biggest companies operating onchain
Get in touch to learn how Blockaid helps teams secure their infrastructure, operations, and users.




