How to Create an Incident Response Plan for Your Onchain Protocol

Onchain protocols are under constant threat from hacks, scams, and exploits.
Even with strong security measures, no system is completely immune—a determined attacker can still find a way in. That’s why, beyond defense, being prepared for a successful attack is critical.
The best way to prepare is by creating a structured incident response plan—a framework that ensures your team can detect, contain, and respond to threats effectively while minimizing damage. Here’s how.
Why every protocol needs an incident response plan
Security isn’t just about preventing attacks—it's about being ready when one happens.
An incident response plan ensures your team can act quickly and decisively when a breach occurs, so you can:
- Reduce financial loses
- Minimize downtime
- Preserve user trust
- Ensure compliance
Without a plan, response efforts can become chaotic, leading to delayed reactions, greater damage, and long-term reputational harm.
Key components of an effective incident response plan
1. Preparation
Goal: Ensure visibility into key areas of risk and be ready to act.
Start by mapping out your critical assets, including things like smart contracts, multisig wallets, and dApp infrastructure.

Once you know what assets matter, determine what components to monitor for each asset type.
For DeFi protocols, monitor liquidity pools, oracle feeds, and token approvals.
For wallets and user interfaces, monitor transactions, dApp connections, and transaction patterns.
For bridges and cross-chain tools, monitor asset flows, validator activity, and cross-chain token movements to detect anomalies effectively.
Finally, define clear incident response roles within your team by assigning responsibilities for:
- Security analysis
- Pausing compromised contracts
- Managing internal and external communications.
This structured approach ensures everyone knows their role during critical moments, minimizing chaos and enabling swift, decisive actions.
2. Monitoring and detection
Goal: Alert the incident response team as early as possible and provide actionable insights to act on.
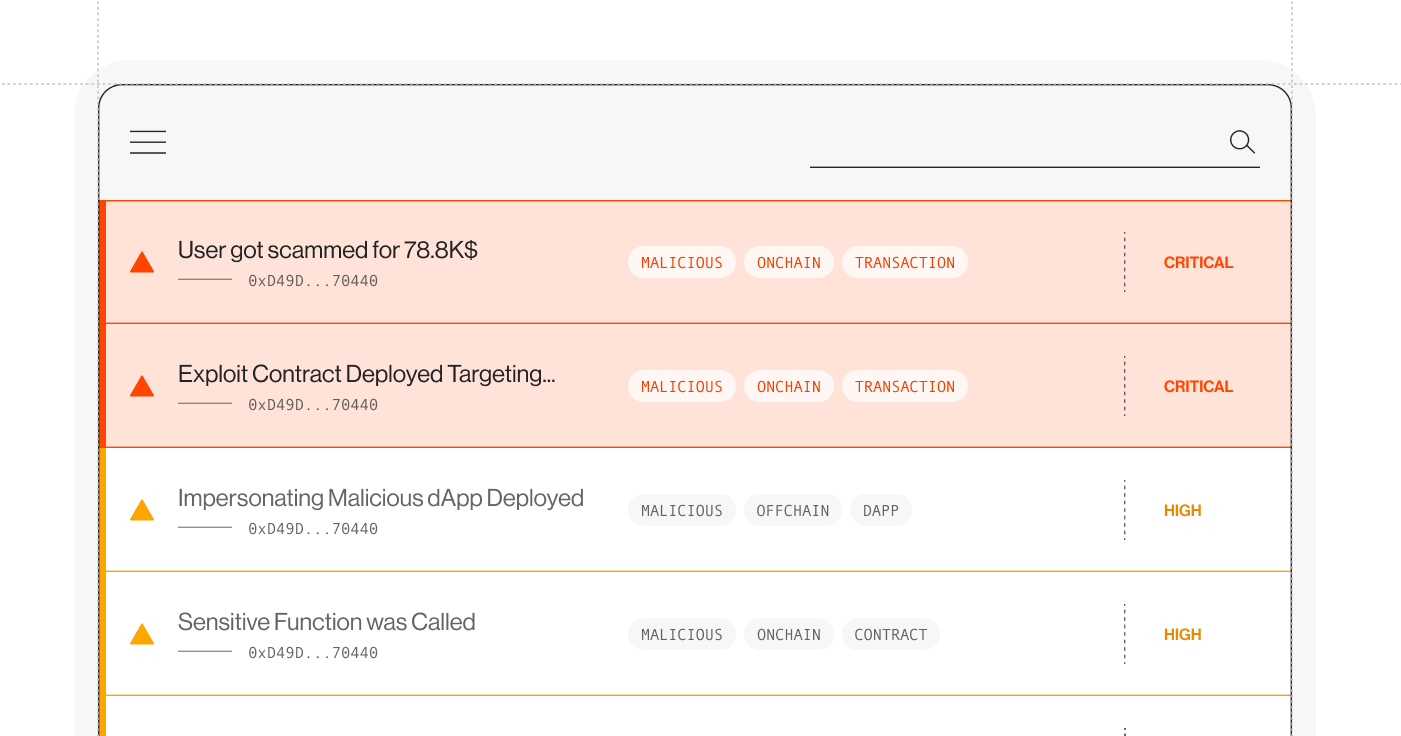
This stage is about understanding what activities to monitor in order to detect potential issues.
What activities to monitor:
- DeFi platforms: Smart contract exploitation attempts, unauthorized multisig approvals, and liquidity pool draining
- Wallets and dApps: Suspicious token approvals, malicious dApp connections, and phishing signatures
- Cross-chain protocols: Bridge anomalies, front-running attempts, and unauthorized validator activity
What changes to detect:
- Transaction volume anomalies: Sudden spikes in transaction activity
- Multiple token approvals: Unusual patterns indicating possible attack setups
- Smart contract state changes: Modifications to contract parameters that could indicate tampering
- User behavior patterns: Unusual signing activity from privileged accounts
3. Response
Goal: Minimize damage, stop unauthorized actions, and give the response team time to investigate.
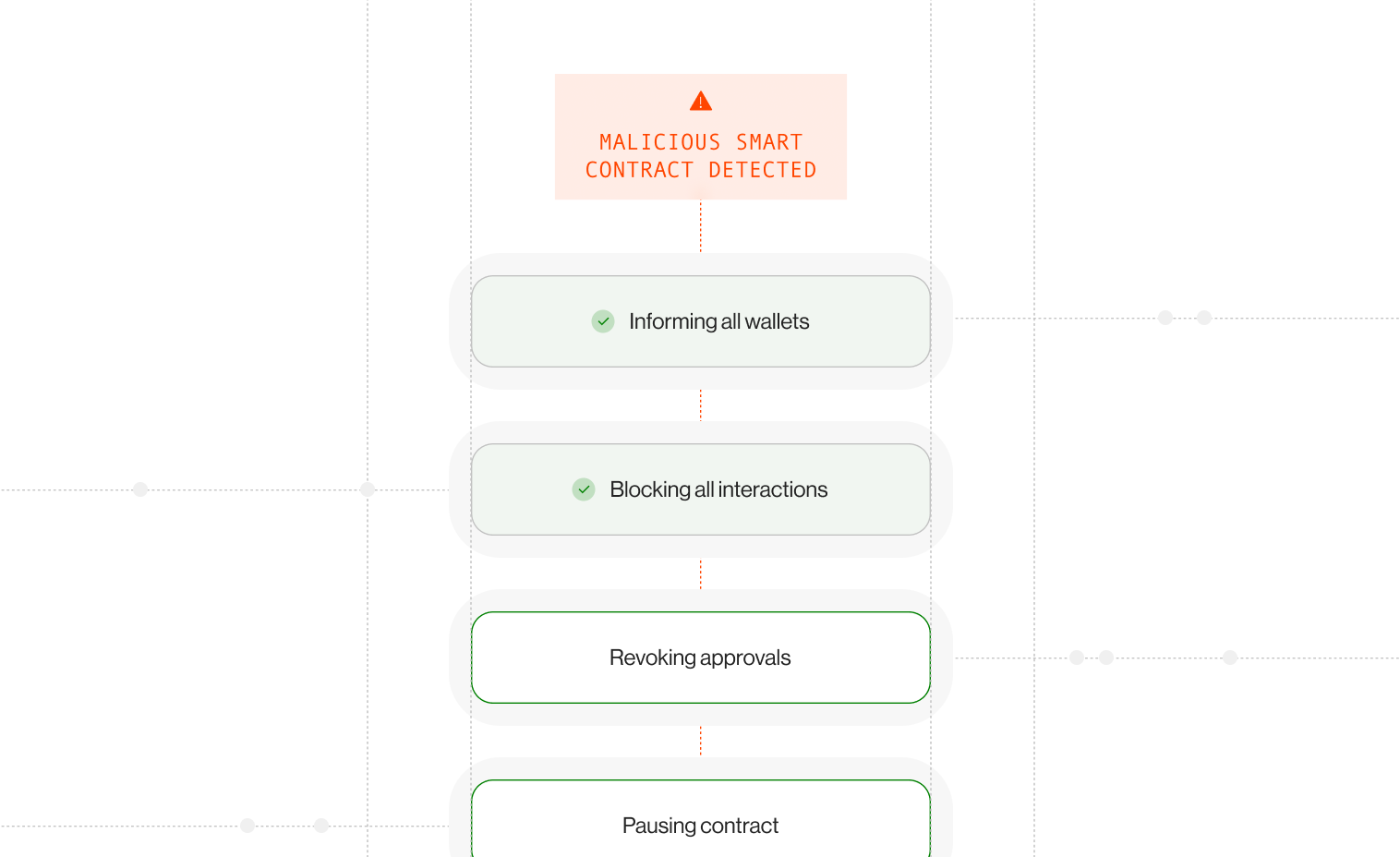
Swift and decisive actions are critical during an active incident to limit damage and maintain control. By focusing on containment and immediate action, your team can prevent further escalation while investigating the root cause.
Key Steps:
- Pause affected contracts: Halt compromised contracts to stop active exploits.
- Revoke token approvals: Cancel risky token permissions to prevent further asset movement.
- Deny multisig signatures: Prevent unauthorized multisig actions by blocking compromised signers.
Automated Workflows:
- Trigger instant alerts to the security team.
- Automate containment steps like freezing withdrawals and blocking further interactions.
4. Eradication
Goal: Completely eliminate the vulnerability and ensure all compromised assets are neutralized, preventing further exploitation.
During and after an attack, there are several key assets to review and harden, including:
Private keys or wallets
- Revoke existing permissions: Cancel all token approvals and access granted to third-party contracts.
- Rotate private keys: Migrate funds to a new, secure wallet and deprecate the compromised key.
- Strengthen access controls: Implement hardware security modules (HSMs) or multisig wallets for key management.
Smart contracts
- Pause the affected contract: If possible, halt the contract to stop further interactions.
- Patch vulnerabilities: Deploy a new contract version if the existing one cannot be patched directly.
- Migrate funds securely: Transfer assets from compromised contracts to secure alternatives.
Governance and multisig accounts
- Deny further signatures: Revoke access for compromised signers and freeze governance actions.
- Reset signer access: Rotate multisig keys and reassign roles based on secure verification.
- Implement enhanced security checks: Require additional layers of approval for critical transactions.
5. Post-mortem and Continuous Improvement
Goal: Turn the incident into a learning opportunity to strengthen defenses, reduce future risks, and improve team readiness.
When incidents occur, they provide a rare chance to identify vulnerabilities and refine your approach to security.
By thoroughly analyzing the timeline of events, uncovering root causes, and evaluating the response plan’s performance, your team can learn from the experience and make meaningful improvements.

To guide your efforts, focus on these key steps:
Reconstruct the timeline: Document the complete sequence of events during the incident, highlighting key actions and timestamps. This provides clarity and a detailed account for analysis.
Determine the root cause: Determine the underlying reasons behind the breach, whether stemming from technical flaws, human error, or process gaps. Identifying these root causes is critical for addressing vulnerabilities.
Assess response: Evaluate how effectively the incident response plan was executed. Identify what worked well and areas that require improvement to enhance readiness for future incidents.
Improve processes: Revise and update response procedures based on lessons learned. Implement stronger monitoring capabilities with granular threat alerts and validate response plans regularly with tabletop simulations and stress tests.
Share findings: Develop internal reports to maintain a clear record of the incident and the response. If appropriate, share summaries with the community to build trust and demonstrate transparency and accountability.
Best practices for a resilient incident response strategy
To keep your protocol secure long-term, the plan must be regularly refined and stress-tested. Here are key best practices to ensure your strategy remains effective:
1. Automate where possible
Manual responses are often too slow in Web3’s fast-paced environment. Automate critical steps like:
- Real-time threat detection.
- Instant alerts to incident response teams.
- Automated containment actions (e.g., pausing contracts, freezing wallets).
2. Define clear roles and responsibilities
A strong response plan clearly defines who handles what during an incident:
- Technical lead: Identifies the threat and recommends technical containment steps.
- Communications lead: Manages public and internal messaging.
- Decision-makers: Ensure rapid approvals for actions like contract pausing or fund freezing.
3. Simulate real-world scenarios
Test your plan through tabletop exercises and live simulations to:
- Identify gaps in response timing.
- Ensure the team knows how to escalate threats.
- Improve collaboration across technical and leadership roles.
4. Continuously update and improve
- After each security event: Review the effectiveness of your response and adjust the plan.
- Track emerging threats: Stay informed about new Web3 attack patterns and update detection criteria.
- Maintain current contact lists: Ensure key personnel are reachable at all times.
5. Transparent communication matters
- During an incident: Provide clear, factual updates to your community.
- After resolution: Share a post-mortem (if appropriate) outlining how the threat was handled and steps taken to prevent recurrence.
Recap
While no protocol can be entirely immune to threats, having a well-defined strategy for monitoring, detection, and response minimizes damage and ensures your team is prepared to act quickly when incidents arise.
By implementing a structured approach, regularly testing your response plan, and automating detection and containment, you can create a more resilient security posture.
The goal is simple: protect your users, assets, and reputation.
Automate your incident response plan with Blockaid
Blockaid offers tools designed to automate key stages of your incident response plan, ensuring faster, more effective reactions to threats across all your assets.
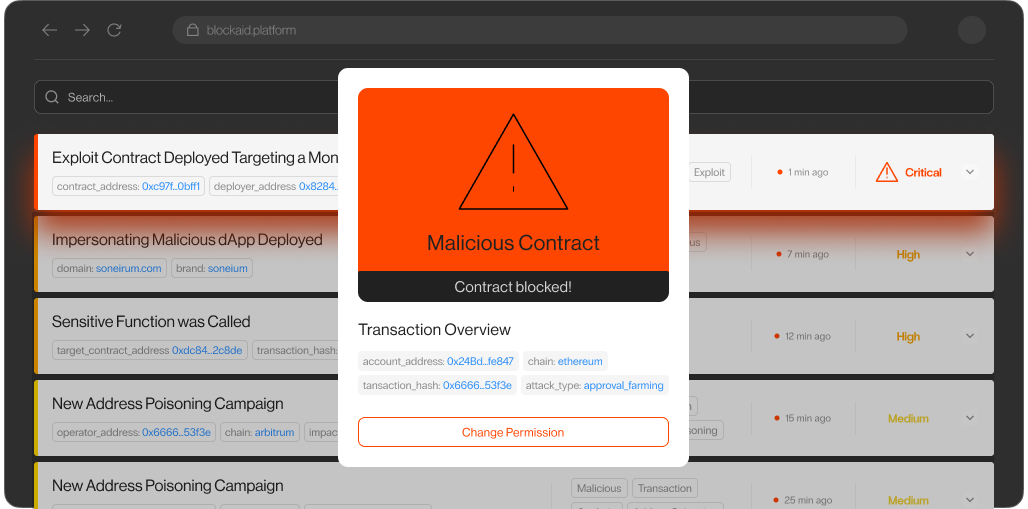
Comprehensive detection and monitoring
Blockaid continuously monitors smart contracts, wallets, liquidity pools, cross-chain bridges, and treasury assets for suspicious activity.
Its detection engine scans onchain activity in real time, identifying risks such as unauthorized token approvals, compromised validators, and abnormal transaction patterns before they escalate.
Automated containment and response
Once a threat is detected, Blockaid can trigger automated response actions based on pre-configured rules. These include:
- Pausing smart contracts to stop further interaction with vulnerable code.
- Revoking token approvals to prevent unauthorized asset transfers.
- Freezing liquidity pools and blocking malicious addresses to limit the spread of an attack.
Seamless alerts and team integration
The platform provides immediate alerts to your security team through channels like Slack, PagerDuty, or custom integrations. This ensures your team stays informed while key containment steps are automatically executed.
Simplifying post-incident analysis
Blockaid also assists with post-incident reporting by tracking all security events, making it easier to conduct detailed post-mortem and continuously improve your response strategy.
By integrating Blockaid, protocols can strengthen their security posture with proactive detection, automated threat responses, and continuous protection across all asset types.
Want to see how Blockaid can help your protocol? Schedule a demo here.
Blockaid is securing the biggest companies operating onchain
Get in touch to learn how Blockaid helps teams secure their infrastructure, operations, and users.




