How Blockaid Secures the $5.7T Stablecoin Economy Against Threats

65% of all crypto scam transactions now involve stablecoins. As a stablecoin issuer, the risks to your business extend far beyond technical vulnerabilities—they threaten reserves, reputation, and the trust that underpins your entire operation.
Why stablecoins issuers face unique challenges
Fraud and asset misuse
Scammers exploit stablecoins' liquidity for financial crimes by leveraging their instant transferability and widespread acceptance across platforms.
Criminals exploit these features to orchestrate large-scale fraud schemes, taking advantage of the difficulty in reversing transactions and the challenge of tracking funds across multiple chains.
They often combine legitimate-looking front operations with complex transaction patterns to obscure their activities, making detection particularly challenging for traditional monitoring systems.
Common scams include:
- Investment scams: Fake token sales and Ponzi schemes
- Elder and romance fraud: Financial exploitation targeting vulnerable users
- Money laundering: Using stablecoins for rapid cross-chain laundering of dirty money
Treasury and reserve vulnerability
Because stablecoin stability relies on fully backed reserves, poor treasury security can lead to:
- Theft of backing assets: Compromised reserve wallets leading to large-scale losses
- Weak access controls: Poorly secured multisignature wallets or admin key leaks
- Reserve mismanagement: Errors or misreporting of collateral assets
- Smart contract exploits: Attackers manipulating the mint/burn mechanisms
Regulatory compliance pressure
Issuers must maintain full visibility and control over their ecosystems to meet increasing compliance demands, including:
- Anti-money laundering (AML) obligations: Detecting and reporting suspicious activity
- Proof of reserves: Ensuring tokens remain fully backed and verifiable
- Legal liability: Issuers must justify enforcement actions with evidence-backed reporting
Ecosystem-wide exposure and cross-chain complexity
Because stablecoins often integrate with multiple DeFi protocols and exchanges, the attack surface area is massive and opens you up to:
- Third-party smart contract vulnerabilities: Exploits in external protocols using the stablecoin
- Cross-chain risks: Bridge vulnerabilities and token duplication issues
- Inconsistent security standards: Varying levels of protection across platform
How Blockaid addresses these challenges
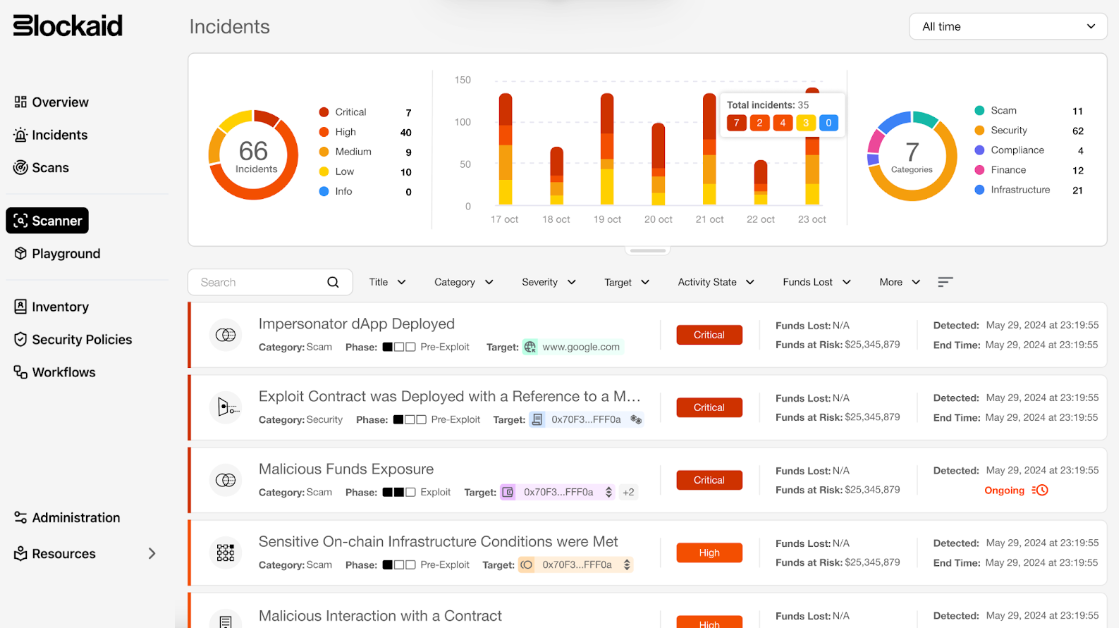
Blockaid’s ODR platform enables stablecoin issuers to monitor, detect, investigate, and respond to threats across their entire token ecosystem, from token activity to protocol infrastructure.
The platform ensures reserves are protected, fraud is prevented, and compliance requirements are met, giving issuers the confidence to operate securely while safeguarding user trust.
By combining real-time monitoring, proactive threat detection, and automated incident response, Blockaid enables issuers to detect and mitigate threats before they escalate.
Monitor token flow and ecosystem activity
Gain full visibility across your entire ecosystem with:
- Real-time tracking of token movements across chains, exchanges, and dApps
- Treasury and reserve monitoring to detect unauthorized outflows
- Surveillance of third-party platforms using the stablecoin for suspicious patterns
Detect threats and malicious activity
Identify risks both within your protocol and across third-party protocols through:
- Identification of malicious entities receiving stablecoins linked to scams
- Suspicious transaction pattern detection, like address poisoning and rapid fund cycling
- Threat intelligence to monitor external threats, like phishing campaigns and malicious dApps
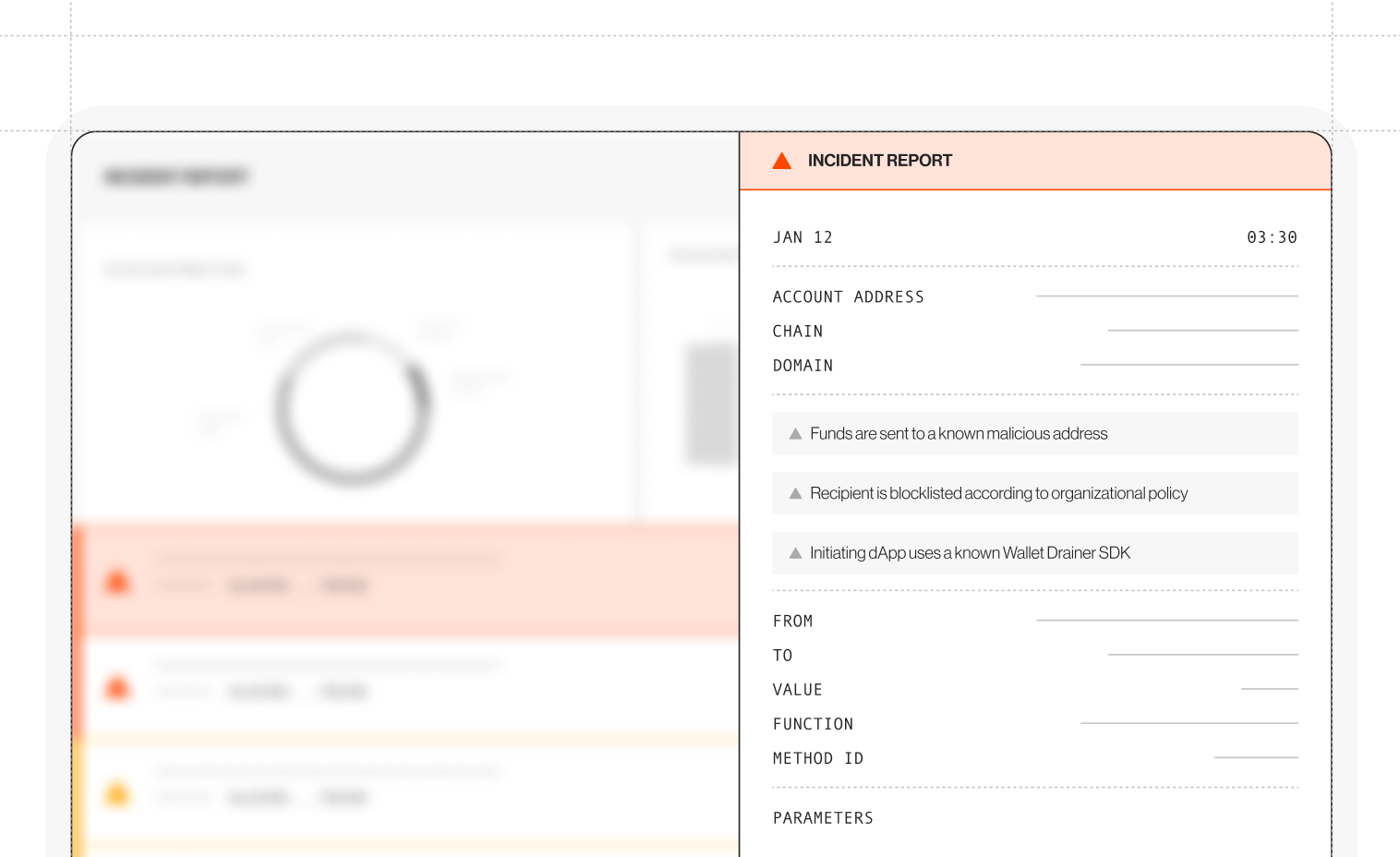
Investigate with actionable evidence
Gain actionable insights and evidence to respond effectively and comply with regulatory needs:
- Comprehensive incident context: Visualize transaction flows, token approvals, and connections to onchain and offchain entities for a complete picture.
- Compliance-ready evidence: Clear records of malicious wallets, exploited vulnerabilities, and associated activity for law enforcement or regulatory audits.
- Integrated workflows: Analyze incidents seamlessly and generate actionable insights to prevent future threats.
Automatically respond to critical incidents
Provide instant, automated protection without requiring manual intervention, by:
- Automatically freezing funds linked to fraudulent activity (when permissions allow)
- Revoking token approvals so malicious wallets can’t interact with your contracts
- Pausing minting and burning contracts to halt token issuance when exploits are detected
Secure protocol contracts and onchain infrastructure
Secure your protocol contracts and infrastructure with:
- Continuous smart contract monitoring for vulnerabilities
- Detection of unauthorized function calls and contract modifications
- Protection for cross-chain bridges and validators from exploitation attempts
Strengthen compliance and regulatory oversight
When incidents and audits happen, make regulatory enforcement less of a headache with:
- Evidence-backed reporting that shows flagged addresses, transaction histories, and security logs
- Automated enforcement for AML standards and high-risk transaction detection
- Alerts for partner exchanges and custodians to monitor for financial crimes
Protect your stablecoin ecosystem with Blockaid
Stablecoin issuers face unique security challenges that demand a proactive, real-time defense strategy. Blockaid has the tools needed to tackle these challenges.
By combining real-time monitoring, proactive threat detection, and automated mitigation, Blockaid empowers stablecoin issuers to secure their entire ecosystem—from circulating token flows to protocol contracts—while simplifying compliance and protecting user trust.
✅ Ready to secure your stablecoin? Book a demo today to discover how Blockaid can help you monitor, detect, and respond to threats across your entire ecosystem.
Blockaid is securing the biggest companies operating onchain
Get in touch to learn how Blockaid helps teams secure their infrastructure, operations, and users.




