Bypasses: How Attackers Evade Transaction Simulation

Transaction Simulation is one of the most effective tools companies can use to help users understand what their transactions will do before they’re executed.
By simulating a transaction, users can catch hidden risks like malicious approvals, phishing attempts, or even unintended asset transfers before it’s too late.
However, attackers know this too. They also know how to bypass simulations which in turn circumvents many of the most common security tools.
This leaves users unknowingly exposed to risks that would otherwise be caught and mitigated.
Here’s why attackers work to create these so-called simulation bypasses, how they look like in practice, and what can be done to stay ahead of these evolving threats.
What is transaction simulation?
Transaction simulation allows security systems to run a transaction in a controlled environment before it’s actually executed.
This means the transaction’s behavior—whether it's transferring assets, approving tokens, or interacting with smart contracts—can be analyzed without committing it onchain.
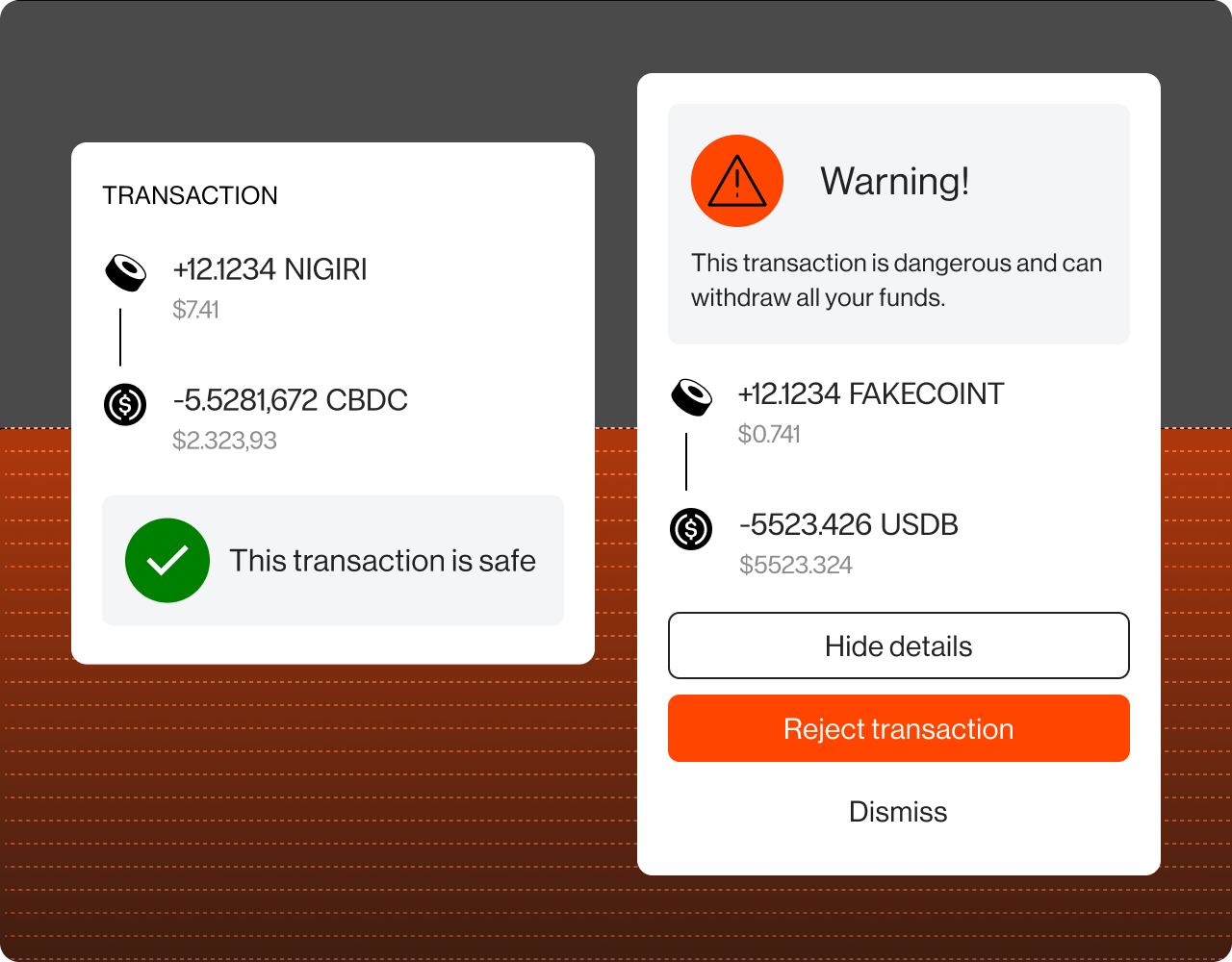
In essence, transaction simulation gives both users and platforms a critical layer of protection by revealing potential risks before they materialize, ensuring greater transparency and trust in the process.
However, it’s important to understand that transaction simulation is not a security solution. While it helps visualize what will happen in a transaction, it doesn’t inherently stop malicious behavior.
Many companies rely on it as if it were a standalone security measure, which can lead to vulnerabilities. Attackers exploit these gaps, knowing they can bypass the simulation and avoid detection.
How bypasses target transaction simulation
A bypass occurs when attackers exploit flaws or bugs in the simulation process to prevent it from analyzing a transaction properly.
These bypasses can take different forms. Some are designed to cause the simulation to fail entirely, triggering errors that leave security systems without the data needed to assess the transaction’s risks.
More complex approaches directly target the simulation, disrupting its ability to flag malicious behavior or allowing the transaction to slip through unnoticed.
In either case, the outcome is the same: the simulation is unable to do its job, leaving the transaction unexamined and exposing users to potential threats.
Real-world example: How a bypass can exploit parsing errors
To see how bypasses work in practice, let’s look at a real-world example of a now-patched bypass that targets the simulation process in a wallet that is not integrated with Blockaid for security..
Note: This specific bypass is an older vulnerability that has since been fixed and no longer poses a threat to users.
In this specific bypass, the attack focuses on exploiting a subtle weakness in simulation of eth_signTypedData_v4 JSON-RPC calls.
In a typical transaction, the user’s wallet will parse the data and simulate the transaction, flagging any malicious behavior—such as unauthorized token approvals or phishing attempts.
Below is an example of how a standard transaction might look and be processed by the wallet:
1window.ethereum.sendAsync({2 "method": "eth_signTypedData_v4",3 "params": [4 ...5 \"message\": {6 ...7 "spender\":\"0x5...\",8 ...9 }"10 ...11 ],12})
In this case, the simulation works as intended, allowing the wallet to issue a warning about any potential risks before the user signs the transaction.
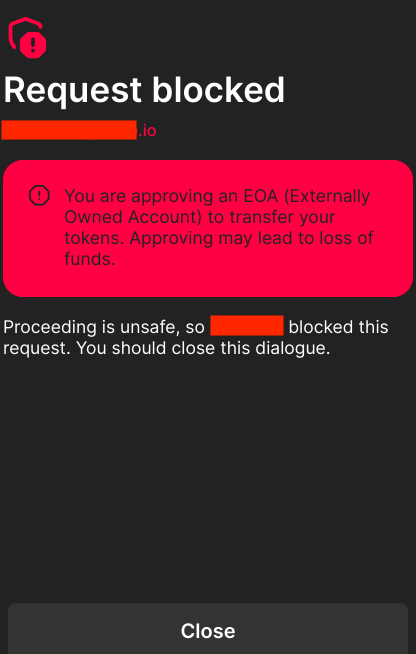
When this JSON-RPC is sent, the wallet flags it as a harmful transaction
However, attackers have discovered a clever way to bypass this security check by exploiting a parsing bug.
If the spender address in the transaction is changed from lowercase (0x) to uppercase (0X), the wallet’s security system fails to display the warning.
While the transaction’s intent hasn’t changed, this subtle alteration causes the wallet to mishandle the parsing, preventing it from flagging the potential risk.
Here’s an example of the bypassed transaction:
1window.ethereum.sendAsync({2 "method": "eth_signTypedData_v4",3 "params": [4 ...5 \"message\": {6 ...7 "spender\":\"0X5...\",8 ...9 }"10 ...11 ],12})
The wallet doesn’t display any warning in this case, leaving the user unaware of the potential danger. This bypass likely occurs due to an error in how the transaction is parsed by the security provider.
When the simulation encounters this specific formatting change, the parsing fails, and the security process is effectively bypassed.
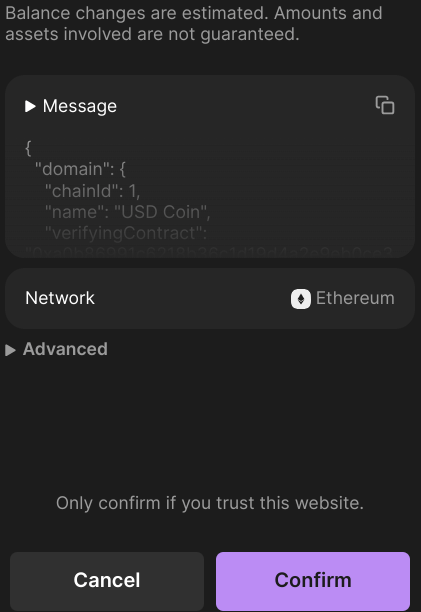
The same transaction - but this time, no warning is shown
This example highlights how attackers can exploit seemingly small technical details to evade detection, emphasizing the need for robust threat detection mechanisms beyond basic simulation checks.
Relying solely on simulation isn’t enough
While simulation is a powerful tool, it’s not enough on its own. To provide stronger security, companies should implement additional layers that address the limitations of simulation.
Here are some key approaches that complement simulation:
Real-time threat detection
Continuous monitoring of off-chain and on-chain activity is key. By tracking new dApps, addresses, and transaction patterns in real time, platforms can catch emerging threats that may bypass a single simulation check.
Transaction validation beyond simulation
Platforms should validate transactions using additional methods. Machine learning models can spot anomalies, while heuristic systems flag suspicious behavior.
This adds an extra layer of protection to catch threats that simulation alone might miss.
Proactive threat hunting
Blockaid was the first web3 security company to create a dedicated team of cybersecurity researchers focused on threat hunting.
This team actively monitors newly deployed malicious dApps and examines their transactions, identifying bypass techniques before they can reach users. By staying ahead of attackers, Blockaid ensures new vulnerabilities are mitigated early on.
Recap
Attackers are getting smarter, finding ways to bypass simulations by exploiting errors or manipulating outputs. Depending solely on simulation leaves dangerous gaps that attackers can and will exploit.
Attackers are constantly searching for new bypasses of security solutions
To truly protect users, platforms need to go beyond simulation with a multi-layered approach. This means implementing real-time threat detection to monitor on-chain activity for new risks as they emerge, proactive threat hunting to uncover bypass techniques and stop them in their tracks, and advanced transaction validation that digs deeper than simulation alone.
In an environment where attackers are constantly evolving, relying on a single layer of defense just isn’t enough.
The key to staying ahead is integrating multiple, proactive security measures that anticipate and neutralize threats before they ever reach users.
Anything less leaves platforms (and users) vulnerable—with attackers ready to exploit those weaknesses.
Blockaid is securing the biggest companies operating onchain
Get in touch to learn how Blockaid helps teams secure their infrastructure, operations, and users.




