Attack Report: The September 2025 NPM Supply Chain Attack

On September 8, 2025, a major supply chain attack was discovered in the JavaScript ecosystem. Popular npm packages—with billions of weekly downloads—were compromised in a targeted effort to hijack crypto transactions.
The malicious packages silently injected code that intercepted wallet addresses and replaced them with attacker-controlled lookalikes—posing a serious threat to anyone interacting with blockchain-based applications.
This attack is one of the most sophisticated examples yet of how traditional software vulnerabilities can be weaponized against crypto users.
Blockaid immediately blocked the majority of malicious addresses across our partner network and continues to monitor for new variants.
The attack vector: popular npm packages used in web3 tooling
The attacker compromised dozens of npm packages deeply embedded in modern front-end stacks—including tools used by dApps, wallets, exchanges, and developer environments.
Affected packages include:
- chalk, supports-color, chalk-template
- ansi-styles, strip-ansi, color-convert, color-name, color-string
- debug, has-ansi, wrap-ansi, slice-ansi, simple-swizzle, is-arrayish
- error-ex, backslash, supports-hyperlinks
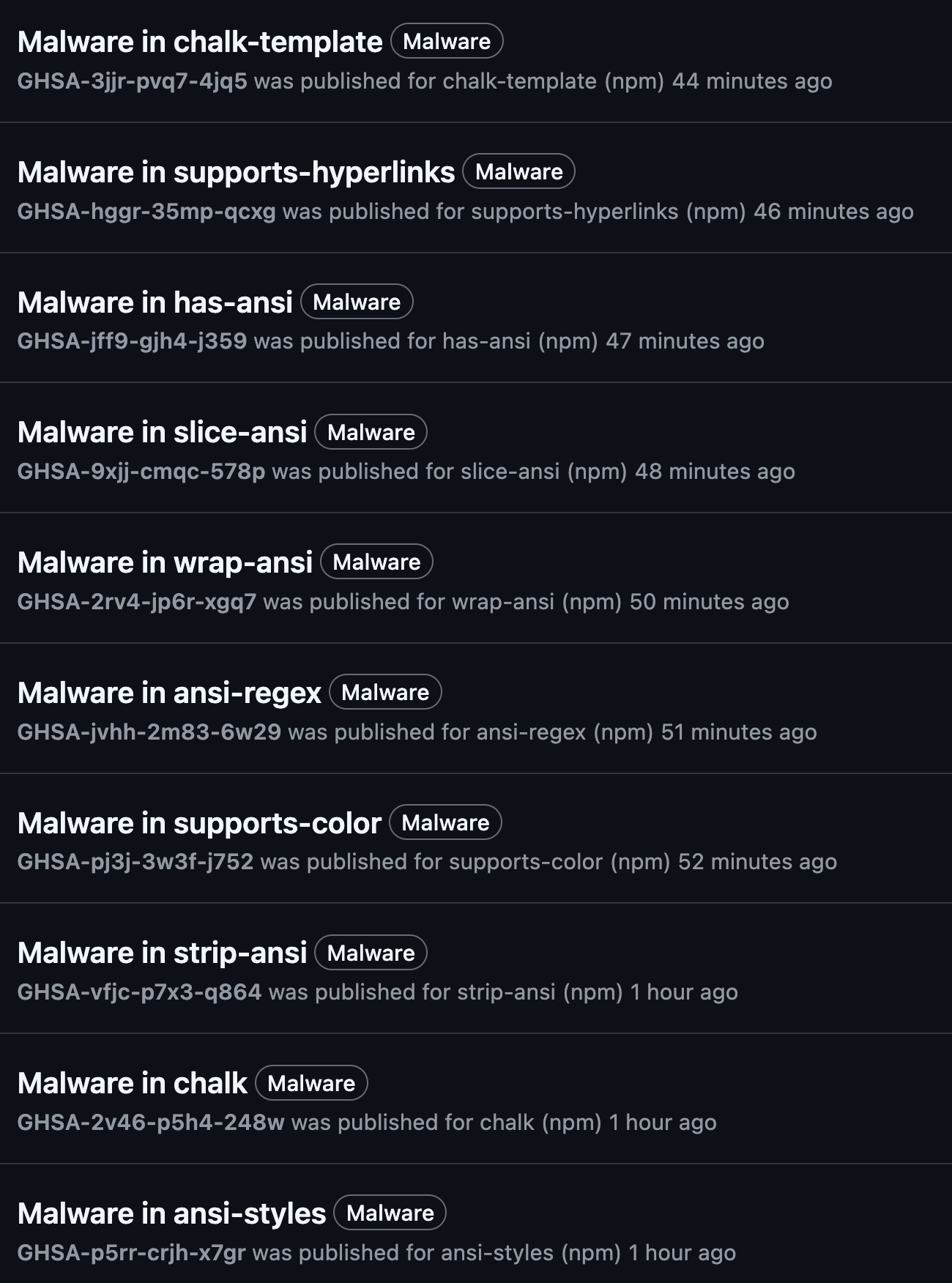
Even projects that didn’t knowingly include these packages may have been affected via transitive dependencies.
How the payload hijacks crypto transactions
This was not a generic malware drop. It was custom-built to target blockchain users. Here’s how it works:
- Monitors network responses in real time
- Scans for crypto wallet addresses
- Silently replaces addresses with attacker-controlled alternatives—crafted to look nearly identical
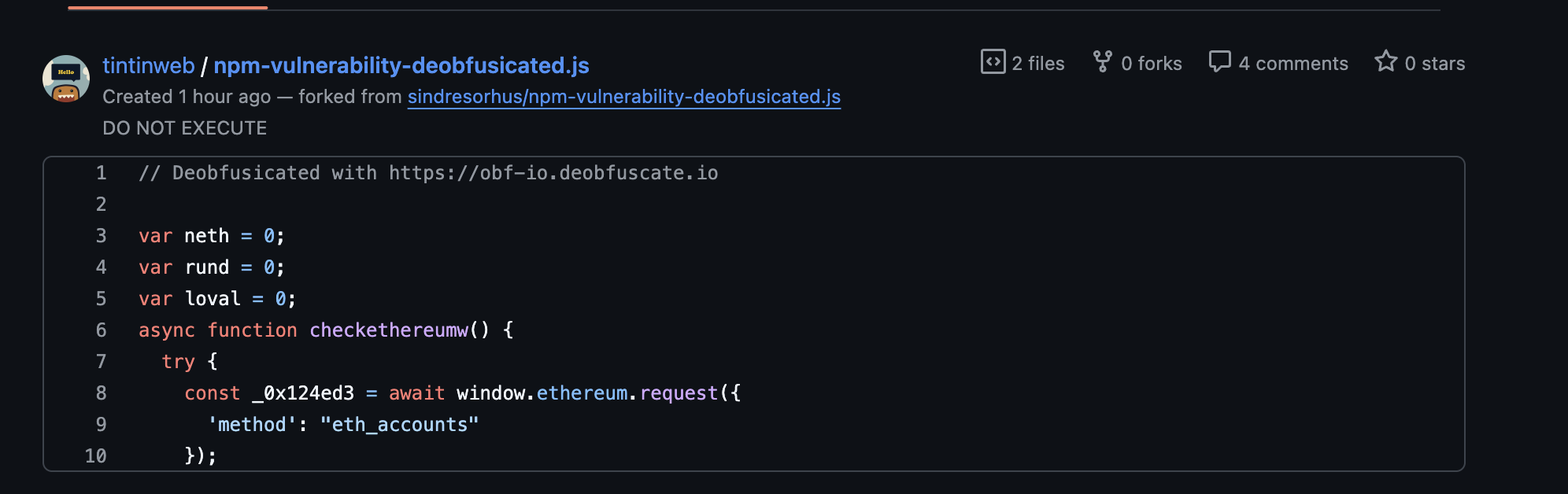
The malicious address is hardcoded into the payload and swaps in without user awareness. No pop-up. No phishing site. Just a silent substitution.
The victim sees the transaction they think they initiated, but the destination wallet has been hijacked.
Identified attacker-controlled wallet addresses
Some of the malicious destination addresses have already been reverse-engineered and disclosed:
Why this attack worked—and how to prevent it
Here’s the key insight: Even with this malware, the attacker still needs the victim to sign the transaction.
That’s why simulation and validation are critical. If you can see what the transaction really does—before signing—you can block the attack.
Blockaid stops this kind of exploit in two core ways:
Blockaid Cosigner: secure what your wallet signs
Cosigner ensures every transaction going through a multisig or MPC wallet is simulated, validated, and policy-checked before it ever reaches the signing threshold. If something looks malicious—or doesn’t match intent—it never goes through.
- Prevents silent hijacks like address substitution
- Applies policy-level guardrails for high-value actions
- Gives ops teams full visibility and control
End User Protection (EUP): protect retail users from invisible threats
Even for individual users, Blockaid simulates and validates every interaction—across major wallets and dApps. That means even if a frontend was compromised by this npm malware, the user would see the real destination address before signing.
- Detects tampered payloads at the final mile
- Works across MetaMask, Ledger, Coinbase Wallet, Trezor, and more
- Already blocking these malicious addresses in production
→ Learn more about End User Protection
What your team should do now
If you’re building in crypto, this is a wake-up call. Here’s what to do immediately:
1. Audit your dependencies
Check if any of the affected npm packages are in your stack, even indirectly through dependencies. Use tools like npm audit, pnpm why, or yarn list.
2. Don’t rely on trust alone
Even widely adopted libraries can be compromised. Assume that code can lie, and verify every interaction onchain.
3. Simulate and validate every transaction
Make sure every transaction—whether retail, institutional, or internal—gets simulated, validated, and checked before any signing action. If you’re not doing both, you’re exposed.
The bigger picture: crypto teams need supply chain-aware security
This attack is a textbook example of how traditional software supply chain vulnerabilities are now being used to exploit web3.
It’s not just phishing or protocol bugs anymore. Every line of code you use is part of your attack surface.
Blockaid exists to close that gap—by securing every onchain interaction before damage is done.
Need support?
Our threat intelligence team is monitoring this campaign and deploying updated protections across our entire partner ecosystem.
If you’re a wallet, dApp, exchange, or platform that needs help responding to this or similar threats, reach out to our team. We’re here to protect you—and your users—before harm is done.
Blockaid is securing the biggest companies operating onchain
Get in touch to learn how Blockaid helps teams secure their infrastructure, operations, and users.




