Attack Report: Lottie Player supply chain attack

On October 30th, at 8:19 PM UTC, Blockaid systems detected a supply chain attack affecting dApps and websites that used the lottie-player npm package.
After a couple of hours, the incident was resolved by Lottie, with the malicious versions removed from NPM and a new, clean version deployed to ensure that all sites using the latest version were secured. We detected approximately 400 websites that were affected by this attack but estimated that many more were impacted.
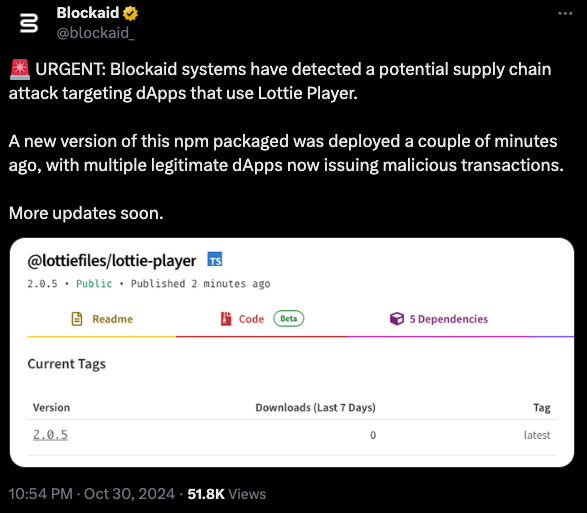
Within minutes of the latest package version release, our monitoring systems identified malicious transactions originating from multiple dApps incorporating this dependency.
After a couple of hours, the incident was resolved by Lottie, with the malicious versions removed from NPM and a new, clean version deployed to ensure that all sites using latest as their version were secured.
During the attack, Blockaid had detected 400~ websites that were affected by this attack, but our estimation is that many more were impacted.
Not all of them were web3-related – our detection identified websites by companies like TOSHIBA, Dream11, Ingenico, and more.
However, since the malicious payload was a wallet drainer and not any other form of malware, we believed that only crypto users were at risk.
Timeline
Here are the key moments from the start of the attack to the patch/fix deployed:
8:12 PM GMT, 30 Oct 2024 - a new version (2.0.5) of @lottiefiles/lottie-player was deployed by an attacker. This version contains a wallet drainer (using Ace Drainer SDK).
8:19 PM GMT, 30 Oct 2024 - Blockaid frontend attack alerts were triggered by a dApp scan. In the following minutes, additional dApps were detected as malicious and automatically flagged.
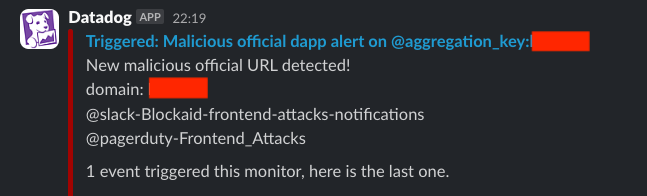
Due to the large volume of dApps, an on-call procedure triggered a team of engineers to investigate. They confirmed that the dApps were under attack, and conducted a payload analysis - correctly identifying lottie-player.js as the culprit.
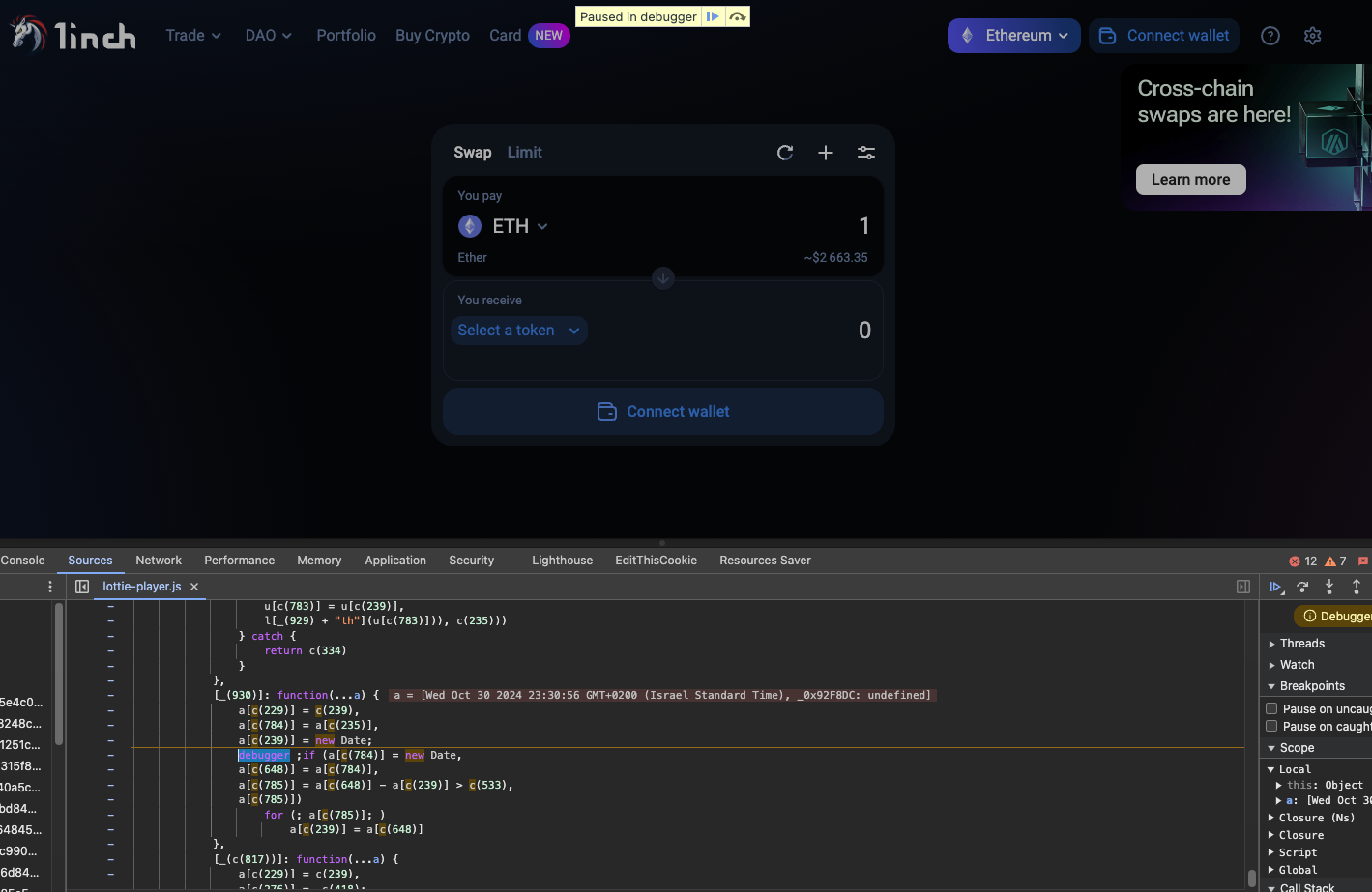
After checking npm, they have observed that a new, malicious version was published just 10 minutes earlier - raising the suspicion that this is another supply chain attack, like the one that impacted Ledger Connect Kit.
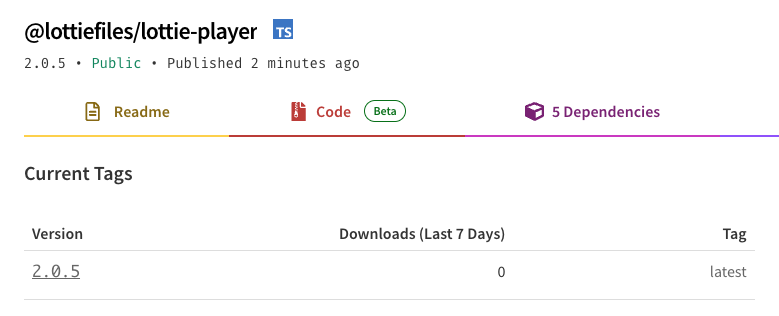
8:54 PM GMT, 30 Oct 2024 - After confirming that the package contains malicious code, Blockaid issued a community alert via X. We have also started contacting affected projects, like 1inch, and reached out to LottieFiles via their socials.
10:18 PM GMT, 30 Oct 2024 - Lottie VP of Engineering @jawish confirmed on GitHub that they were aware of the issue and were working to resolve it.
11:13 PM GMT, 30 Oct 2024 - @jawish confirmed that they’d removed the compromised account and had pushed a new, clean version (2.0.8).
11:47 PM GMT, 30 Oct 2024 - Affected versions were removed from npm.
Details
What’s a supply chain attack?
Supply chain attacks target a fundamental vulnerability in software: our shared reliance on common code and libraries.
Rather than attacking a single application, attackers inject malicious code directly into widely used dependencies—the core tools, libraries, and frameworks that countless applications depend on.
This type of attack can be thought of as poisoning a well that supplies water to an entire town – rather than targeting individual endpoints, the attacker compromises a central resource that everything depends on.
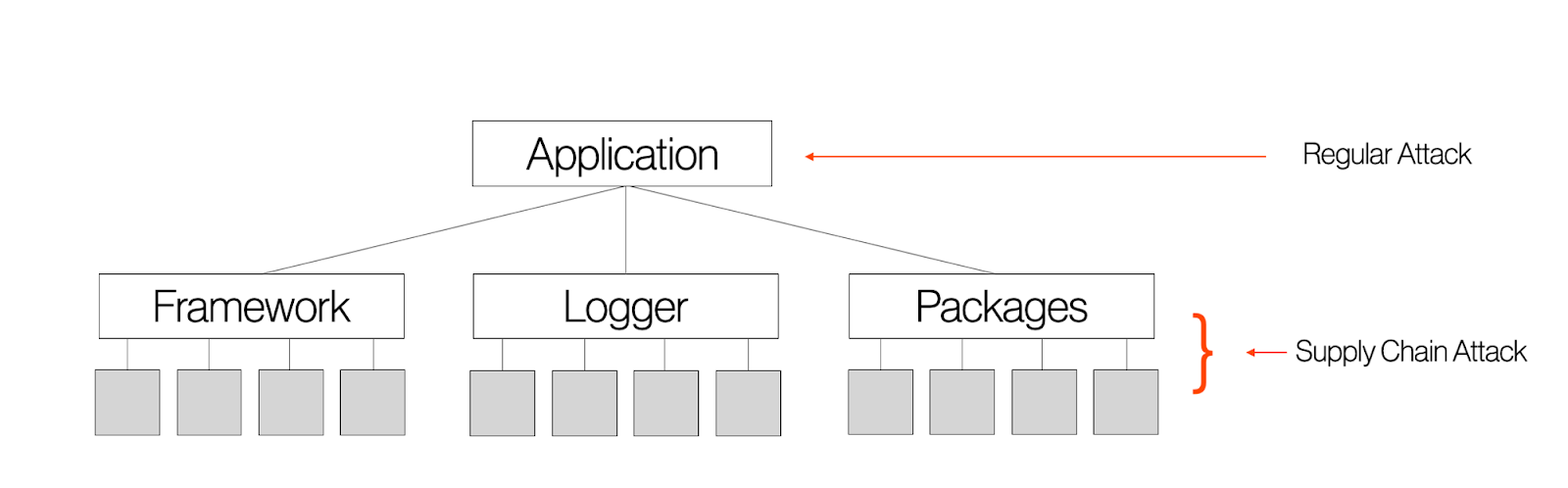
The scope of a supply chain attack is vast—a “one hit to rule them all” event. When a trusted package or library is compromised, every application that relies on it becomes vulnerable.
This means that a single attack can propagate across hundreds or even thousands of sites, pushing malicious code to users across the web3 ecosystem - or even outside of it - in one sweeping strike.
Attack overview
The malicious payload was pushed to npm using compromised tokens belonging to Lottie maintainer @Aidosmf.
The malicious version of the package retained the original functionality, but had introduced a large blob of web3-related code.
Based on Blockaid threat intelligence, we were able to confirm that this payload is a version of the Ace Drainer DaaS (Drainer-as-a-Service).
This attribution was made possible due to Blockaid Threat Hunting efforts, which found unique code and communication patterns matching methods used by Ace.
Potential impact
Supply chain attacks of this nature presented a widespread risk due to their propagation through trusted dependencies. Fortunately, Blockaid detected this incident within minutes, meaning that many users were never in interaction with the affected websites.
For the few who proceeded to connect their wallets despite Blockaid’s warnings, our transaction scanning feature saved assets worth around 750,000 USD from being stolen.
Conclusion
This incident is a stark reminder: in web3, even trusted tools can be exploited within minutes.
As attackers turn to supply chains to reach end users, fast detection and response are critical for mitigating impact.
Moving forward, proactive security measures across every layer of the ecosystem aren’t just protective—they’re essential to building the trust needed for web3 to thrive.
Blockaid is securing the biggest companies operating onchain
Get in touch to learn how Blockaid helps teams secure their infrastructure, operations, and users.




