Deep Dive into Address Poisoning

While the decentralized nature of blockchains brings remarkable opportunities, it also poses significant risks. As open networks of value, blockchains allow anyone to send anything to anyone—a quality that makes them susceptible to various forms of spam transactions, much like how email spam floods our inboxes.
Amidst this flood of spam, various attack vectors have emerged, with one of the most prominent being address poisoning, a deceptive technique used by attackers to target unsuspecting users and platforms, leveraging the openness of blockchain to deceive and steal.
With a significant rise in the volume of these attacks in the last couple of months (a rise that is caused by various factors, not least of which is the steep decline in gas prices), understanding how they work and how to protect yourself is more crucial than ever.
Let's dive into the mechanics, effectiveness, and prevention of address poisoning attacks to help you stay safe in the evolving crypto landscape.
What is an Address Poisoning Attack?
An address poisoning attack is a deceptive tactic malicious actors use to trick users into sending cryptocurrency to an incorrect address. Unlike phishing attacks, which often involve social engineering and malicious websites, address poisoning operates within the blockchain's infrastructure. The attacker aims to "poison" a user's address book by flooding it with addresses controlled by the attacker, hoping the user will mistakenly send funds to one of these fraudulent addresses in the future.
Why Address Poisoning Attacks are Effective
Address poisoning attacks are particularly effective due to several factors:
- User Behavior: Many users rely on their transaction history for convenience, especially when sending funds to frequent contacts. The attack leverages this behavior, increasing the likelihood of a mistake.
- Low Detection Rate: These attacks can be subtle and difficult to detect, as they don't involve overtly malicious actions like phishing. The transactions are legitimate, making it harder for users to recognize the threat.
- Cost-Effective for Attackers: Since the attacker only needs to send small amounts of cryptocurrency to poison the address book, the cost of conducting such an attack is relatively low, and the potential returns are high.
Deep dive - How Address Poisoning Attacks Work
Address poisoning attacks exploit the human tendency to reuse addresses from recent transactions. Here's a step-by-step breakdown of how these attacks typically unfold:
- Initial Setup and Monitoring: The attacker identifies a notable wallet, such as a high-value or frequently used address, and monitors its activity on the blockchain. They use blockchain explorers and analytics tools to track movements and identify wallet transaction patterns.
- Generating Similar Addresses: The attacker generates an address that resembles one that the victim often interacts with. We will dive into this process in a minute.
- Issuing Transactions: The attacker sends small amounts of cryptocurrency from the fake, similar address to the target's wallet. These transactions are small enough to avoid suspicion but significant enough to appear in the target’s wallet transaction history.
- Poisoning the Address Book: As these transactions are recorded on the blockchain, the attacker’s addresses appear in the target’s transaction history. These addresses are crafted to look very similar to the legitimate addresses the target has previously interacted with.
- User Mistake: When the target user decides to send a large amount of cryptocurrency, they often refer to their transaction history for convenience. Due to the address poisoning, the user sees multiple transactions involving addresses similar to the legitimate recipient's address. In a hurry or due to oversight, the user mistakenly selects one of the attacker’s addresses.
- Successful Theft: The target user sends the large transaction to the attacker’s address instead of the intended recipient. The funds are now under the attacker's control, and the target realizes the mistake only after the transaction is irreversible.
By monitoring notable wallets and generating similar-looking addresses, attackers significantly increase the chances of a successful address-poisoning attack. This method relies on the natural human behavior of reusing addresses and the randomness of address creation to deceive users into making costly mistakes.
Creating Similar Addresses in a Random Address Generation System
Even though the address creation process is random, attackers can generate addresses until they find one that closely matches a target address. This process is computationally intensive and may require generating millions of addresses, but it is still feasible enough to be used by attackers.
Here’s how attackers can do it:
- Target an Existing Address: Identify an address frequently used by the victim.
- Generate Addresses: Use the Bitcoin address creation method to generate many addresses.
- Check Similarity: Compare each generated address to the target address. If the similarity criteria are met (e.g., same prefix or suffix), the address is kept; otherwise, it is discarded.
- Repeat: Continue generating addresses until a suitably similar one is found.
Example Code for Address Similarity
Here’s a simplified Python example demonstrating how an attacker might search for similar addresses:
1def generate_bitcoin_address():2 [...]34def find_similar_address(target_prefix):5 while True:6 address = generate_bitcoin_address()7 if address.startswith(target_prefix):8 return address910target_address = '1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa'11similar_address = find_similar_address(target_address[:5])12print(f"Target Address: {target_address}")13print(f"Similar Address: {similar_address}")
This code continually generates Bitcoin addresses until it finds one with the same prefix as the target address. While this example uses a prefix for simplicity, more sophisticated similarity metrics can be used.
Step-by-Step Attack Scenario
Let's analyze a possible attack scenario involving a USDT whale, their intended recipient, and a malicious actor.
Step 1: Identifying the Target
A malicious actor identifies a USDT whale who frequently transfers large amounts of USDT. This whale regularly sends funds to a specific recipient, such as an exchange or a cold wallet.
Step 2: Setting Up Malicious Addresses
The attacker generates multiple USDT addresses under their control. These addresses are created to resemble the legitimate recipient's address closely but differ slightly in some characters.
Step 3: Poisoning the Address Book
The attacker sends a small amount of the native token to the whale's address using the generated addresses. These transactions are insignificant and intended to blend into the whale's transaction history without raising suspicion.
Step 4: Exploiting the Poisoned Address
When the whale decides to send a large sum of USDT to their intended recipient, they check their transaction history for convenience. Due to the address poisoning, the whale sees multiple transactions involving addresses similar to the recipient's address. In a hurry or due to oversight, the whale selects one of the attacker's addresses.
Step 5: Successful Theft
The whale sends the large USDT transaction to the attacker's address instead of the intended recipient. The funds are now under the attacker's control, and the whale realizes the mistake only after the transaction is irreversible.
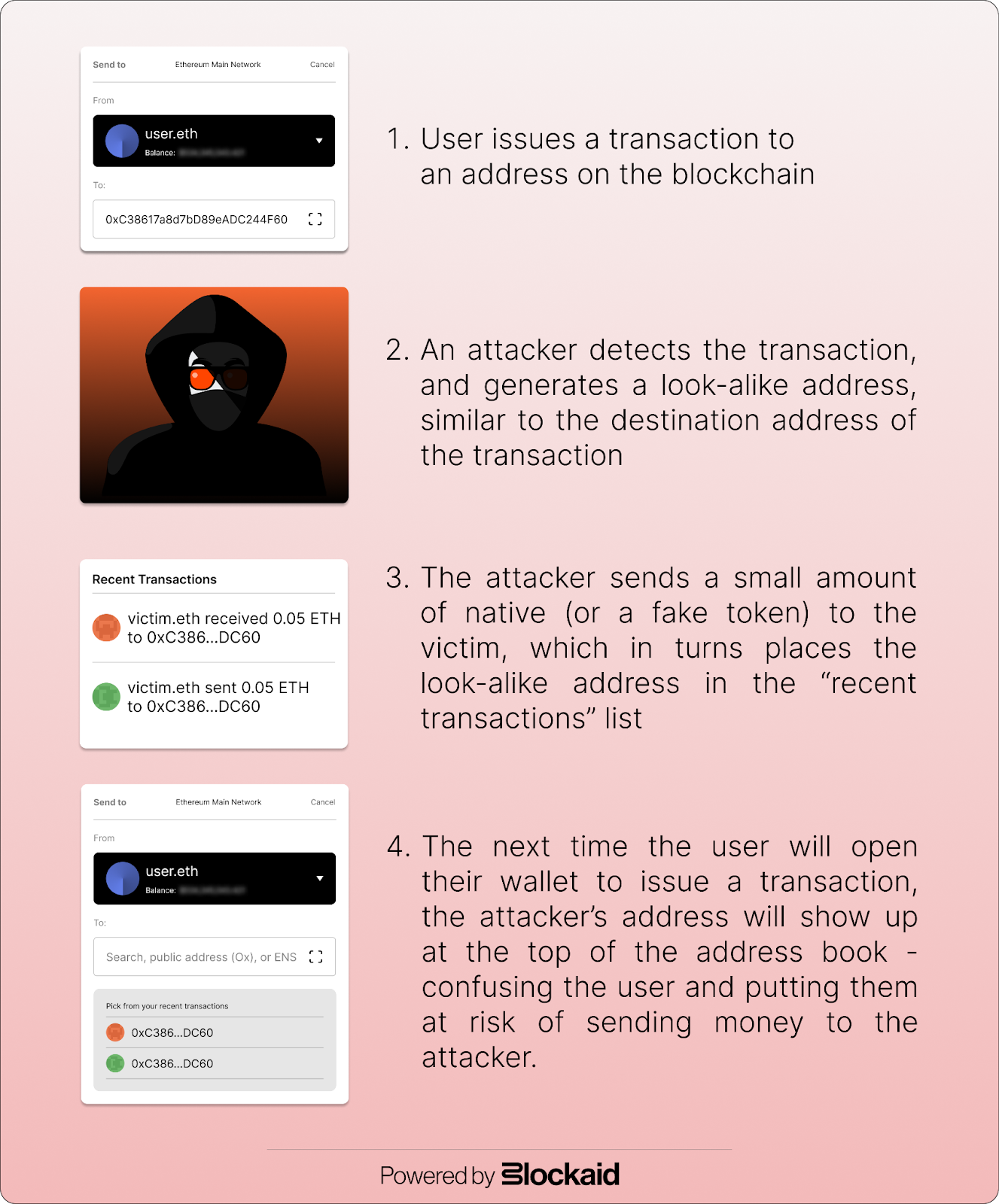
Event Spoofing and Address Poisoning
Now that we understand the structure of an address-poisoning attack, let's look at another method attackers use to enhance its effectiveness: manipulating blockchain events to create a false sense of legitimacy around the attacker’s addresses. This method is called Event spoofing.
Event spoofing is a technique attackers use to manipulate blockchain events, creating a false sense of legitimacy around their addresses. By exploiting the design of smart contract standards, like ERC-20, attackers can generate fake transaction events that appear genuine. This deceptive tactic enhances the effectiveness of address-poisoning attacks by making malicious addresses seem involved in legitimate activities, thereby increasing the likelihood that users will mistakenly trust and interact with them.
How Event Spoofing Works
- Creating Fake Events: The attacker creates fake events on the blockchain, which appear legitimate. In the context of ERC-20 tokens, these events can be token transfers or approvals.
- Associating Events with Poisoned Addresses: These fake events are associated with both the attacker's and the victim's addresses, making them appear to have been involved in legitimate transactions.
- Boosting Credibility: When the target user reviews their transaction history or related blockchain events, the attacker's addresses seem more credible due to their involvement in multiple activities, increasing the likelihood of the user selecting the wrong address.
Exploiting ERC-20 Token Events
To better understand Event spoofing, let's look at how it is used within the Ethereum ecosystem.
ERC-20 is a popular standard for creating tokens on the Ethereum blockchain. It includes several standard functions and events that help ensure interoperability between tokens and platforms. One of the core features of ERC-20 is the Transfer event, which logs when tokens are transferred from one address to another.
Here's how the Transfer event is defined in the ERC-20 standard:
event Transfer(address indexed from, address indexed to, uint256 value);
This event is emitted whenever a token transfer occurs. It includes the sender's address (from), the recipient's address (to), and the amount of tokens transferred (value).
The issue with this structure is that nothing enforces that the from address included in the event is the address that issued the transaction that triggered it! For example, consider this simple contract:
1contract FakeTransfer {2 event Transfer(address indexed from, address indexed to, uint256 value);34 function emitFakeTransfer(address _from, address _to, uint256 _value) public {5 emit Transfer(_from, _to, _value);6 }7}
As you can see, this contract will emit the same Transfer event as any other ERC20 - but it will do so for any address you want - which can be used by attackers to increase the chances of a successful address poisoning attack - Let's see how, step by step:
- Deploying a Malicious Contract: The attacker deploys a smart contract designed to emit fake
Transferevents. This contract does not need to follow the full ERC-20 standard; it only needs to emit theTransferevents. To make things worse, attackers can also name the contract to resemble a well-known one, like USDT or DAI. - Emitting Fake Transfer Events: The attacker triggers the malicious contract to emit
Transferevents, in which tokens are transferred from the attacker's address to various legitimate addresses - including the victim's. These events are recorded on the blockchain and visible to users and applications. - Manipulating Wallet Histories: When users or applications (such as block explorers) query the blockchain for transaction histories, they see these fake
Transferevents. The attacker's addresses appear frequently - in some cases, the victim might see interaction between their address and the fake address - giving them a veneer of legitimacy.
As you can see, by using event spoofing methods, attackers can make address poisoning attacks much more convincing, and as such - much harder to defend against.
Address Poisoning in the wild
To wrap this subject up, let's review how an address poisoning attack looks in practice.
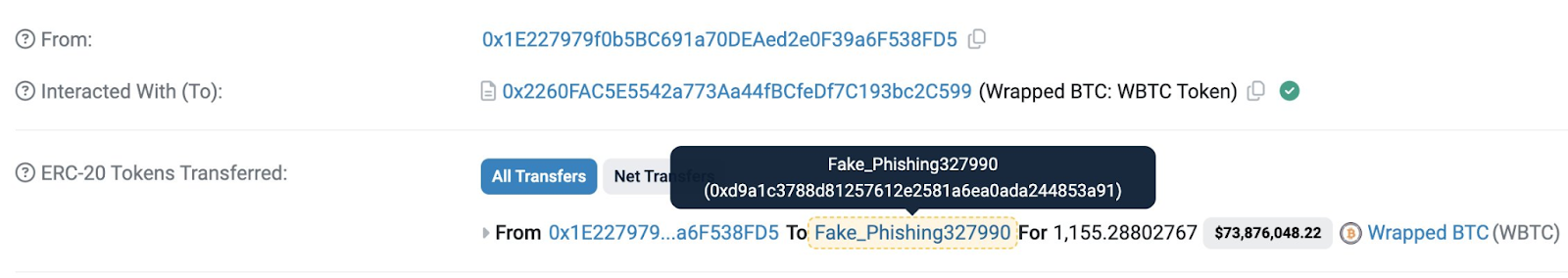
On May 3rd, 2024, an address poisoning attack, which also used event spoofing, enabled an attacker to steal 1155 WBTC tokens - worth over $68M. While the funds were ultimately returned, this incident is a good case study to examine how these attacks look in a real-world attack scenario. Let's take a look.
Step 1: Target acquisition
The attacker notices a movement from an address holding millions of dollars worth of tokens. Usually, attackers use bots that monitor new transactions being added to the chain to find targets worth pursuing.
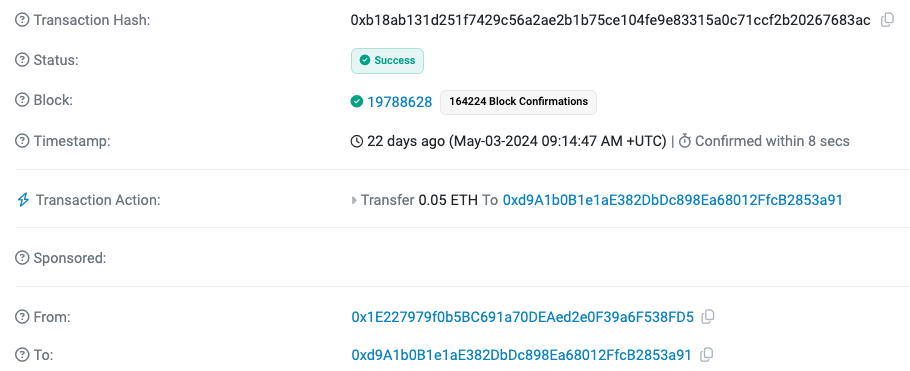
Step 2: Generate a similar address
To start the attack, the attacker has generated an address similar to the one that the WBTC holder has legitimately interacted with:
Legitimate address: 0xd9A1b0B1e1aE382DbDc898Ea68012FfcB2853a91
Attacker's address: 0xd9a1c3788d81257612e2581a6ea0ada244853a91
As you can see, the first on-chain activity of the fake address was a few minutes after the original transaction:
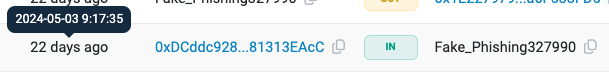
Step 3: Event Spoofing
The attacker employs an Event spoofing attack to gain additional credibility and potentially further poison the victim's wallet, creating a malicious contract named ERC-20 Token. Then, the attacker issues a transaction that causes many token transfer events to be emitted - all of them are spoofed transfers of a scam token worth nothing.
In one of them, the spoofed event shows a transfer of funds from the WBTC holder (the victim) to the fake, attacker-controlled address.
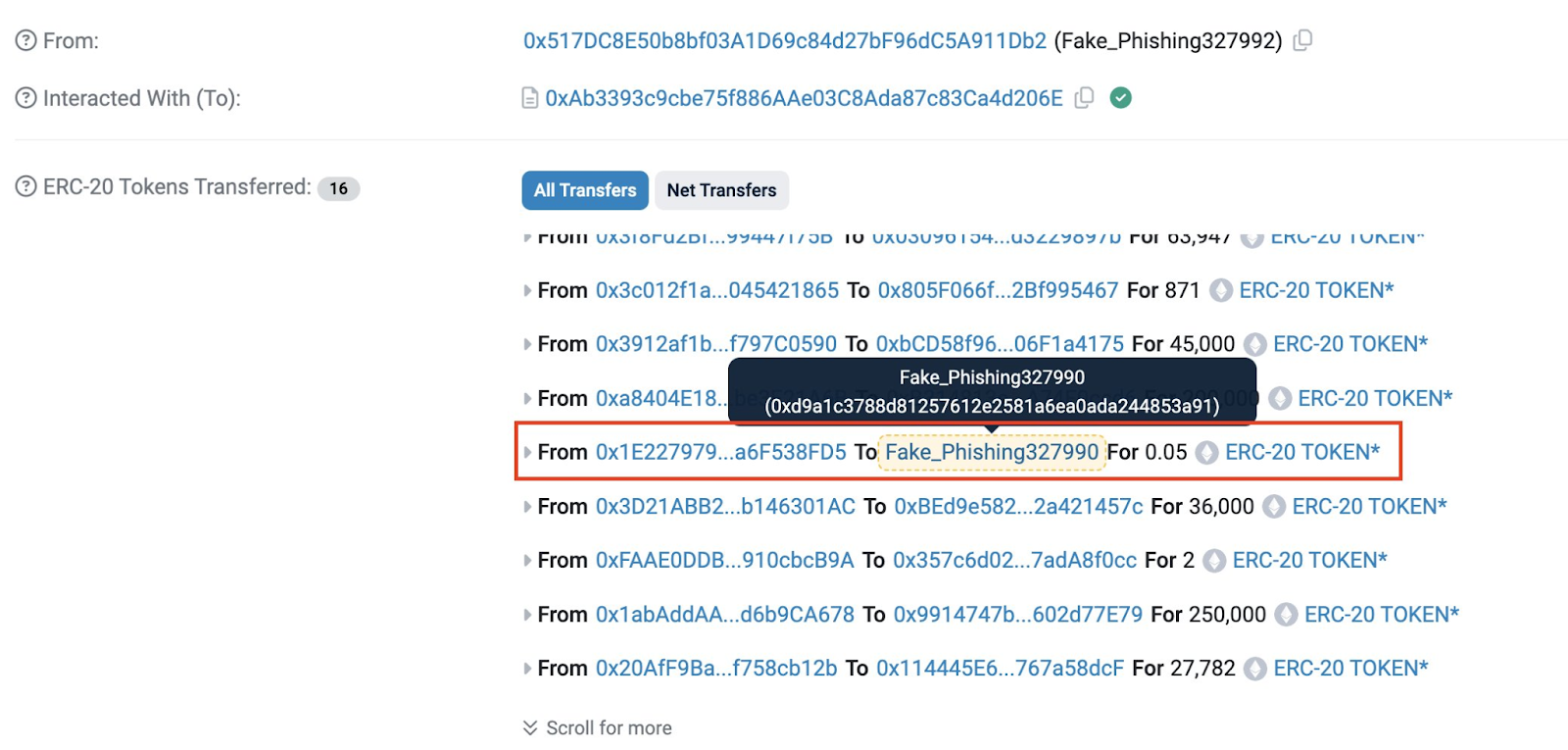
Step 4: Dusting Attack
Finally, to get into the victim's address book, the attacker-controlled address sends a tiny dust transaction involving 0.00021 ETH (worth less than a dollar).
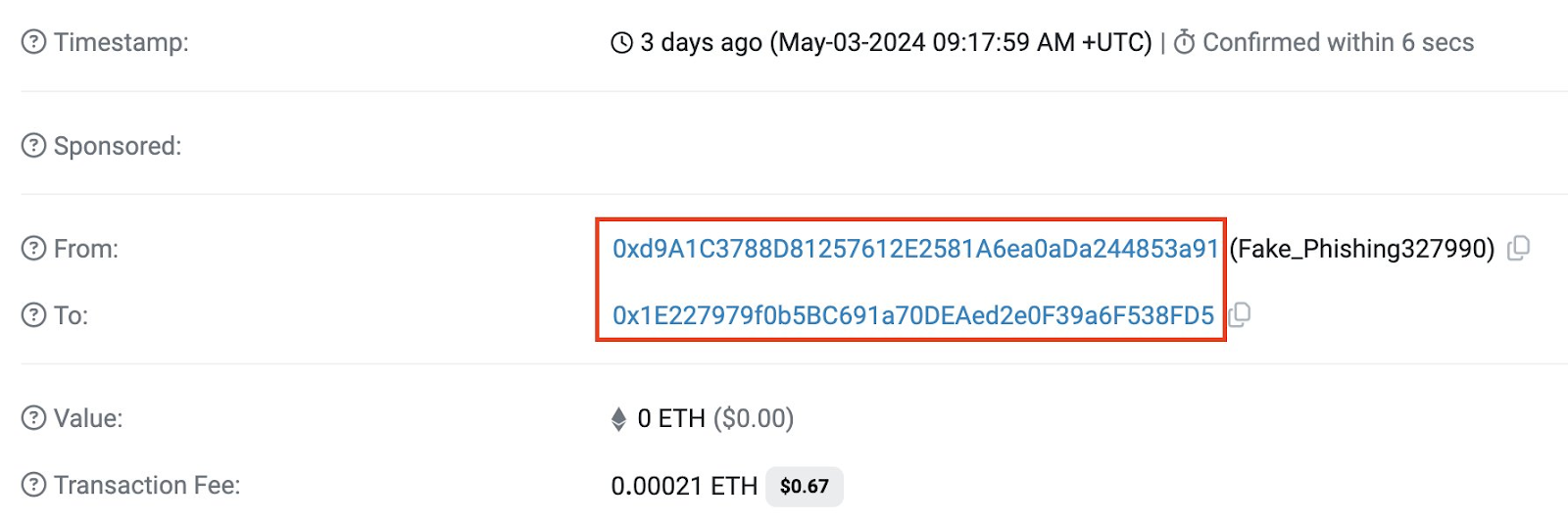
Step 5: User mistake
Finally, the WBTC holder goes to make another transaction. They go into their address book and see an address similar to the one they've just interacted with - 0xd9a1...853a91.
They check their recent transactions and see that they've just sent 0.05 of something to this address. Since they've just sent 0.05 ETH to another address that looks very similar, they figure that this is the address that they want to interact with. They send their WBTC to this address... and lose it.
The attacker has succeeded.
Mitigations for Address Poisoning and Event Spoofing
As you can see, address poisoning attacks are way more sophisticated than you might think. As such, preventing address poisoning attacks, including those that leverage event spoofing, requires a combination of user vigilance and platform-level protections. As a user, here are some strategies to mitigate the risk:
- Verify Addresses Carefully: Always double-check the address before sending cryptocurrency. Avoid relying solely on your transaction history and use address books or contact lists for frequent transactions.
- Use Wallet Features: Some wallets offer features like labeling addresses and creating whitelists. Utilize these features to ensure you're sending funds to the correct addresses.
- Monitor Transaction History: Regularly review your transaction history for any suspicious activity. If you notice small, unsolicited transactions, it could indicate an address poisoning attempt.
In addition to these steps, which are placing the responsibility on users to protect themselves, platforms can also act to keep users safe by implementing security tools: tools and services that detect and prevent address poisoning attacks. These tools can monitor unusual transaction patterns and alert users to threats, or even hide these addresses from the user interface to keep the user from ever interacting.
Conclusion
Understanding the current landscape of address poisoning attacks, including event spoofing, is crucial for developing effective strategies to mitigate these risks and protect the crypto community.
These attacks are sophisticated and ever-evolving, and no user should ever think, "This won't happen to me!" as this is the first step towards an error that would leave you helpless.
Stay informed, be vigilant, and leverage available tools to safeguard your digital assets.
Blockaid is securing the biggest companies operating onchain
Get in touch to learn how Blockaid helps teams secure their infrastructure, operations, and users.




